...
RouterBOARDs with Atheros switch chips can be used for 802.1Q Trunking. This feature in RouterOS v6 is supported by QCA8337, Atheros8316, Atheros8327, Atheros8227 and Atheros7240 switch chips.
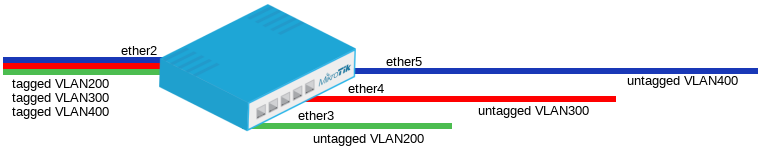
In this example ether3, ' ether4 and ether5 interfaces are access ports, while ether2 is a trunk port. VLAN IDs for each access port: ether3 - 200, ether4 - 300, ether5 - 400.
Switch together the required ports:
| Code Block | ||
|---|---|---|
| ||
/interface bridge
add name=bridge1
/interface bridge port
add bridge=bridge1 interface=ether2 hw=yes
add bridge=bridge1 interface=ether3 hw=yes
add bridge=bridge1 interface=ether4 hw=yes
add bridge=bridge1 interface=ether5 hw=yes |
...
| Note |
|---|
...
By default, the bridge interface is configured with |
Add VLAN table entries to allow frames with specific VLAN IDs between ports:
| Code Block | ||
|---|---|---|
| ||
/interface ethernet switch vlan
add ports=ether2,ether3 switch=switch1 vlan-id=200
add ports=ether2,ether4 switch=switch1 vlan-id=300
add ports=ether2,ether5 switch=switch1 vlan-id=400 |
...
Assign vlan-mode and vlan-headermode header mode for each port and also default-vlan-id on ingress for each access port:
| Code Block | ||
|---|---|---|
| ||
/interface ethernet switch port
set ether2 vlan-mode=secure vlan-header=add-if-missing
set ether3 vlan-mode=secure vlan-header=always-strip default-vlan-id=200
set ether4 vlan-mode=secure vlan-header=always-strip default-vlan-id=300
set ether5 vlan-mode=secure vlan-header=always-strip default-vlan-id=400 |
...
- Setting
vlan-mode=secureensures strict use of VLAN table. - Setting
vlan-header=always-stripfor access ports removes VLAN header from frame when it leaves the switch chip. - Setting
vlan-header=add-if-missingfor trunk port adds VLAN header to untagged frames. default-vlan-idspecifies what VLAN ID is added for untagged ingress traffic of the access port.
...
| Note |
|---|
VLAN Example 2 (Trunk and Hybrid Ports)
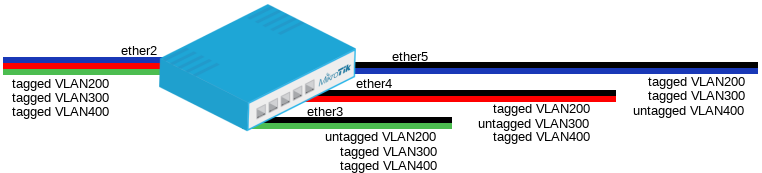
VLAN Hybrid ports which can forward both tagged and untagged traffic are . This configuration is supported only by some Gigabit switch chips (QCA8337, Atheros8327).
Switch together the required ports:
| Code Block | ||
|---|---|---|
| ||
/interface bridge
add name=bridge1
/interface bridge port
add bridge=bridge1 interface=ether2 hw=yes
add bridge=bridge1 interface=ether3 hw=yes
add bridge=bridge1 interface=ether4 hw=yes
add bridge=bridge1 interface=ether5 hw=yes |
...
| Note |
|---|
...
By default, the bridge interface is configured with |
Add VLAN table entries to allow frames with specific VLAN IDs between ports.
| Code Block | ||
|---|---|---|
| ||
/interface ethernet switch vlan
add ports=ether2,ether3,ether4,ether5 switch=switch1 vlan-id=200
add ports=ether2,ether3,ether4,ether5 switch=switch1 vlan-id=300
add ports=ether2,ether3,ether4,ether5 switch=switch1 vlan-id=400 |
...
In switch port menu set vlan-mode on all ports and also default-vlan-id on planned hybrid ports:
| Code Block | ||
|---|---|---|
| ||
/interface ethernet switch port
set ether2 vlan-mode=secure vlan-header=leave-as-is
set ether3 vlan-mode=secure vlan-header=leave-as-is default-vlan-id=200
set ether4 vlan-mode=secure vlan-header=leave-as-is default-vlan-id=300
set ether5 vlan-mode=secure vlan-header=leave-as-is default-vlan-id=400 |
...
vlan-mode=securewill ensure strict use of VLAN table.default-vlan-idwill define VLAN for untagged ingress traffic on port.- In QCA8337 and Atheros8327 chips when
vlan-mode=secureis used, it ignores switch portvlan-headeroptions. VLAN table entries handle all the egress tagging/untagging and works asvlan-header=leave-as-ison all ports. It means what comes in tagged, goes out tagged as well, onlydefault-vlan-idframes are untagged at the egress of port.
Management access configuration
In these examples there will be shown examples for multiple scenarios, but each of these scenarios require you to have switched ports. Below you can find how to switch multiple ports:
| Code Block | ||
|---|---|---|
| ||
/interface bridge
add name=bridge1
/interface bridge port
add interface=ether1 bridge=bridge1 hw=yes
add interface=ether2 bridge=bridge1 hw=yes |
...
| Note |
|---|
...
By default, the bridge interface is configured with |
In these examples it will be assumed that ether1 is the trunk port and ether2 is the access port, for configuration as the following:
| Code Block | ||
|---|---|---|
| ||
/interface ethernet switch port
set ether1 vlan-header=add-if-missing
set ether2 default-vlan-id=100 vlan-header=always-strip
|
...
/interface ethernet switch vlan
add ports=ether1,ether2,switch1-cpu switch=switch1 vlan-id=100 |
...
Tagged
In order to make the device accessible only from a certain VLAN, you need to create a new VLAN interface on the bridge interface and assign an IP address to it:
| Code Block | ||
|---|---|---|
| ||
/interface vlan
add name=MGMT vlan-id=99 interface=bridge1 |
...
/ip address
add address=192.168.99.1/24 interface=MGMT |
...
Specify from which interfaces it is allowed to access the device:
| Code Block | ||
|---|---|---|
| ||
/interface ethernet switch vlan
add ports=ether1,switch1-cpu switch=switch1 vlan-id=99 |
...
| Note |
|---|
...
Only specify trunk ports in this VLAN table entry, it is not possible to allow access to the CPU with tagged traffic through an access port since the access port will tag all ingress traffic with the specified |
When VLAN table is configured, you can enable vlan-mode=secure to limit access to the CPU:
| Code Block | ||
|---|---|---|
| ||
/interface ethernet switch port
set ether1 vlan-header=add-if-missing vlan-mode=secure
set ether2 default-vlan-id=100 vlan-header=always-strip vlan-mode=secure
set switch1-cpu vlan-header=leave-as-is vlan-mode=secure |
...
Untagged
In order to make the device accessible from the access port, create a VLAN interface with the same VLAN ID as set in default-vlan-id, for example VLAN 100, and add an IP address to it:
| Code Block | ||
|---|---|---|
| ||
/interface vlan
add name=VLAN100 vlan-id=100 interface=bridge1
|
...
/ip address
add address=192.168.100.1/24 interface=VLAN100 |
...
Specify which access (untagged) ports are allowed to access the CPU:
| Code Block | ||
|---|---|---|
| ||
/interface ethernet switch vlan
add ports=ether1,ether2,switch1-cpu switch=switch1 vlan-id=100 |
...
| Warning |
|---|
...
Most commonly an access (untagged) port is accompanied with a trunk (tagged) port. In case of untagged access to the CPU, you are forced to specify both the access port and the trunk port, this gives access to the CPU from the trunk port as well. Not always this is desired and Firewall might be required on top of VLAN filtering. |
When VLAN table is configured, you can enable vlan-mode=secure to limit access to the CPU:
| Code Block | ||
|---|---|---|
| ||
/interface ethernet switch port
set ether1 vlan-header=add-if-missing vlan-mode=secure
set ether2 default-vlan-id=100 vlan-header=always-strip vlan-mode=secure
set switch1-cpu vlan-header=leave-as-is vlan-mode=secure |
...
| Note |
|---|
...
To setup management port using untagged traffic on a device with the Atheros7240 switch chip, you will need to set |
Untagged from tagged port
It is possible to allow access to the device from the trunk (tagged) port with untagged traffic. To do so, assign an IP address on the bridge interface:
| Code Block | ||
|---|---|---|
| ||
/ip address
add address=10.0.0.1/24 interface=bridge1 |
...
Specify which ports are allowed to access the CPU. Use vlan-id that is used in default-vlan-id for switch-cpu and trunk ports, by default it is set to 0 or 1.
| Code Block | ||
|---|---|---|
| ||
/interface ethernet switch vlan
add ports=ether1,switch1-cpu switch=switch1 vlan-id=1 |
...
When VLAN table is configured, you can enable vlan-mode=secure to limit access to the CPU:
| Code Block | ||
|---|---|---|
| ||
/interface ethernet switch port
set ether1 default-vlan-id=1 vlan-header=add-if-missing vlan-mode=secure
set switch1-cpu default-vlan-id=1 vlan-header=leave-as-is vlan-mode=secure |
...
Note:
| Note |
|---|
This configuration example is not possible for devices with the Atheros8316 and Atheros7240 switch chips. |
...
For devices with QCA8337 and Atheros8327 switch chips it is possible to use any other |
See also
- Switch Router
- Basic VLAN Switching
- Bridge Hardware Offloading
- Spanning Tree Protocol
- DHCP Snooping and Option 82
- MTU on RouterBOARD
- Layer2 misconfiguration
- Master-port
- Atheros8316 packet flow diagram
...