...
There are several types of switch chips on Routerboards and they have a different set sets of features. Most of them (from now on "Other") have only the basic "Port Switching" feature, but there are a few with more features:
| Feature | QCA8337 | Atheros8327 | Atheros8316 | Atheros8227 | Atheros7240 | ICPlus175D | MT7621 | RTL8367 | 88E6393X | 88E6191X | 98PX1012 | Other |
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Port Switching | yes | yes | yes | yes | yes | yes | yes | yes | yes | yes | no | yes |
| Port Mirroring | yes | yes | yes | yes | yes | yes | yes | yes | yes | yes | no | no |
| TX limit 1 | yes | yes | yes | yes | yes | no | yes | yes | yes | yes | no | no |
| RX limit 1 | yes | yes | no | no | no | no | yes | yes | yes | yes | no | no |
| Host table | 2048 entries | 2048 entries | 2048 entries | 1024 entries | 2048 entries | 2048 entries 2 | 2048 entries | 2048 entries | 16k entries | 16k entries | no | no |
| Vlan table | 4096 entries | 4096 entries | 4096 entries | 4096 entries | 16 entries | no | 4096 entries 3 | 4096 entries 3 | 4096 entries 3 | 4096 entries 3 | no | no |
| Rule table | 92 rules | 92 rules | 32 rules | no | no | no | no | no | 256 | no | no | no |
...
- For QCA8337, Atheros8327, Atheros8316, Atheros8227, and Atheros7240 the Tx/Rx rate limits can be changed with
bandwidthproperty on"/interface ethernet"menu, see more details in the Ethernet manual. For RTL8367, 88E6393X, 88E6191X, and MT7621 Tx/Rx rate limit can be changed withegress-rateandingress-rateproperties on "/interface ethernet switch port" menu. - MAC addresses are learned up to the specified number, but the content of a switch host table is not available in RouterOS and static host configuration is not supported.
- Bridge HW vlan-filtering was added in the RouterOS 7.1rc1 (for RTL8367) and 7.1rc5 (for MT7621) versions. The switch does not support other
ether-type0x88a8 or 0x9100 (only 0x8100 is supported) and notag-stacking. Using these features will disable HW offload.
| Note |
|---|
Cloud Router Switch (CRS) series devices have highly advanced switch chips built-in, they support a wide variety of features. For more details about switch chip capabilities on CRS1xx/CRS2xx series devices check the CRS1xx/CRS2xx series switches manual, for CRS3xx series devices check the CRS3xx, CRS5xx series switches, and CCR2116, CCR2216 routers manual. |
...
Port Switching
In order to setup set up port switching on non-CRS series devices, check the Bridge Hardware Offloading page.
...
Ether1 port on RB450G/RB435G/RB850Gx2 devices have has a feature that allows it to be removed/added to the default switch group, this setting is available on the /interface ethernet switch menu. By default ether1 port will be included in the switch group.
...
| Property | Description |
|---|---|
| switch-all-ports (no | yes; Default: yes) | Changes ether1 switch group only on RB450G/RB435G/RB850Gx2 devices.
|
...
| Property | Description |
|---|---|
| mirror (no | yes; Default: no) | Whether to send a frame copy to mirror-target port from a frame with a matching MAC destination address (matching destination or source address for CRS3xx series switches) |
...
| Property | Description |
|---|---|
| vlan-mode (check | disabled | fallback | secure; Default: disabled) | Changes the VLAN lookup mechanism against the VLAN Table for ingress traffic.
|
| vlan-header (add-if-missing | always-strip | leave-as-is; Default: leave-as-is) | Sets action which is performed on the port for egress traffic.
|
| default-vlan-id (auto | integer: 0..4095; Default: auto) | Adds a VLAN tag with the specified VLAN ID on all untagged ingress traffic on a port, should be used with vlan-header set to always-strip on a port to configure the port to be the access port. For hybrid ports default-vlan-id is used to tag untagged traffic. If two ports have the same default-vlan-id, then VLAN tag is not added since the switch chip assumes that traffic is being forwarded between access ports. |
...
VLAN table specifies certain forwarding rules for packets that have a specific 802.1Q tag. Those rules are of higher priority than switch groups configured using the Bridge Hardware Offloading feature. Basically, the table contains entries that map specific VLAN tag IDs to a group of one or more ports. Packets with VLAN tags leave the switch chip through one or more ports that are set in the corresponding table entry. The exact logic that controls how packets with VLAN tags are treated is controlled by a vlan-mode parameter that is changeable per switch port.
...
| Property | Description |
|---|---|
| disabled (no | yes; Default: no) | Enables or disables switch VLAN entry. |
| independent-learning (no | yes; Default: yes) | Whether to use shared-VLAN-learning (SVL) or independent-VLAN-learning (IVL). |
| ports (name; Default: none) | Interface member list for the respective VLAN. This setting accepts comma-separated values. e.g. ports=ether1,ether2. |
| switch (name; Default: none) | Name of the switch to for which the respective VLAN entry is intended for. |
| vlan-id (integer: 0..4095; Default:) | The VLAN ID for certain switch port configurationconfigurations. |
| Note |
|---|
Devices with MT7621, RTL8367, 88E6393X, 88E6191X switch chips support HW offloaded vlan-filtering in RouterOS v7. VLAN-related configuration on the "/interface ethernet switch" menu is not available. |
...
| Property | Description |
|---|---|
| copy-to-cpu (no | yes; Default: no) | Whether to send a packet copy to switch CPU port |
| mirror (no | yes; Default: no) | Whether to send a packet copy to mirror-target port |
| new-dst-ports (name; Default: none) | Changes the destination port as specified, multiple ports allowed, including a switch CPU port. An empty setting will drop the packet. When the parameter is not used, the packet will be accepted |
| new-vlan-id (integer: 0..4095) | Changes the VLAN ID to the specified value or adds a new VLAN tag if one was not already present (the property only applies to the Atheros8316 switch chip) |
| new-vlan-priority (integer: 0..7) | Changes the VLAN priority field (priority code point) |
| rate (integer: 0..4294967295) | Sets ingress traffic limitation (bits per second) for matched traffic, can only be applied to the first 32 rule slots (the property only applies to Atheros8327/QCA8337 switch chips) |
| redirect-to-cpu (no | yes; Default: no) | Changes the destination port of a matching packet to the switch CPU |
Conditions The conditions part is controlled by the rest of the parameters:
| Property | Description |
|---|---|
| disabled (no | yes; Default: no) | Enables or disables switch rule |
| dscp (integer: 0..63) | Matching DSCP field of the packet |
| dst-address (IP address/Mask) | Matching destination IP address and mask |
| dst-address6 (IPv6 address/Mask) | Matching destination IPv6 address and mask |
| dst-mac-address (MAC address/Mask) | Matching destination MAC address and mask |
| dst-port (integer: 0..65535) | Matching destination protocol port number or range |
| flow-label (integer: 0..1048575) | Matching IPv6 flow label |
| mac-protocol (802.2 | arp | homeplug-av | ip | ipv6 | ipx | lldp | loop-protect | mpls-multicast | mpls-unicast | packing-compr | packing-simple | pppoe | pppoe-discovery | rarp | service-vlan | vlan | or 0..65535 | or 0x0000-0xffff) | Matching particular MAC protocol specified by protocol name or number (skips VLAN tags if any) |
| ports (name) | Name of the interface on which the rule will apply on the received traffic, multiple ports are allowed |
| protocol (dccp | ddp | egp | encap | etherip | ggp | gre | hmp | icmp | icmpv6 | idpr-cmtp | igmp | ipencap | ipip | ipsec-ah | ipsec-esp | ipv6 | ipv6-frag | ipv6-nonxt | ipv6-opts | ipv6-route | iso-tp4 | l2tp | ospf | pim | pup | rdp | rspf | rsvp | sctp | st | tcp | udp | udp-lite | vmtp | vrrp | xns-idp | xtp | or 0..255) | Matching particular IP protocol specified by protocol name or number |
| src-address (IP address/Mask) | Matching source IP address and mask |
| src-address6 (IPv6 address/Mask) | Matching source IPv6 address and mask |
| src-mac-address (MAC address/Mask) | Matching source MAC address and mask |
| src-port (0..65535) | Matching source protocol port number or range |
| switch (switch group) | Matching switch group on which will the rule apply |
| traffic-class (0..255) | Matching IPv6 traffic class |
| vlan-id (0..4095) | Matching VLAN ID (the property only applies to theAtheros8316, Atheros8327, QCA8337 switch chips) |
| vlan-header (not-present | present) | Matching VLAN header, whether the VLAN header is present or not (the property only applies to the Atheros8316, Atheros8327, QCA8337 switch chips) |
| vlan-priority (0..7) | Matching VLAN priority (priority code point) |
...
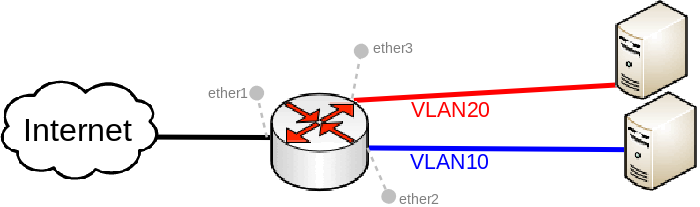
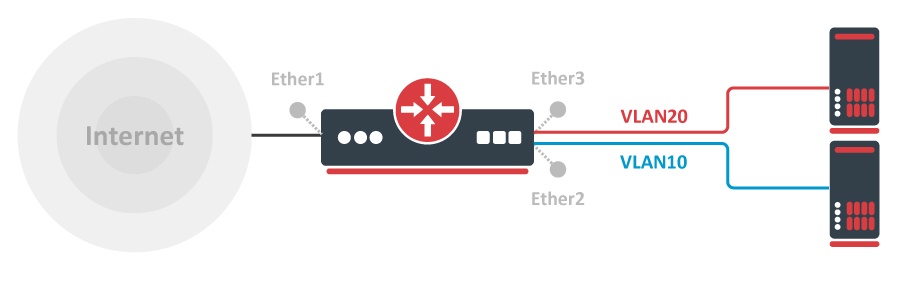
Many MikroTik's devices come with a built-in switch chip that can be used to greatly improve overall throughput when configured properly. Devices with a switch chip can be used as a router and a switch at the same time, this gives you the possibility to use a single device instead of multiple devices for your network.
For this type of setup to work, you must switch all required ports together
| Code Block | ||
|---|---|---|
| ||
/interface bridge add name=bridge1 /interface bridge port add bridge=bridge1 interface=ether2 hw=yes add bridge=bridge1 interface=ether3 hw=yes |
Create a VLAN interface for each VLAN ID and assign an IP address to it:
| Code Block | ||
|---|---|---|
| ||
/interface vlan add interface=bridge1 name=VLAN10 vlan-id=10 add interface=bridge1 name=VLAN20 vlan-id=20 /ip address add address=192.168.10.1/24 interface=VLAN10 add address=192.168.20.1/24 interface=VLAN20 |
Setup a DHCP Server for each VLAN:
| Code Block | ||
|---|---|---|
| ||
/ip pool add name=POOL10 ranges=192.168.10.100-192.168.10.200 add name=POOL20 ranges=192.168.20.100-192.168.20.200 /ip dhcp-server add address-pool=POOL10 disabled=no interface=VLAN10 name=DHCP10 add address-pool=POOL20 disabled=no interface=VLAN20 name=DHCP20 /ip dhcp-server network add address=192.168.10.0/24 dns-server=8.8.8.8 gateway=192.168.10.1 add address=192.168.20.0/24 dns-server=8.8.8.8 gateway=192.168.20.1 |
Enable NAT on the device:
| Code Block | ||
|---|---|---|
| ||
/ip firewall nat add action=masquerade chain=srcnat out-interface=ether1 |
Add each port to the VLAN table and allow these ports to access the CPU in order to make DHCP and routing work:
| Code Block | ||
|---|---|---|
| ||
/interface ethernet switch vlan add independent-learning=yes ports=ether2,switch1-cpu switch=switch1 vlan-id=10 add independent-learning=yes ports=ether3,switch1-cpu switch=switch1 vlan-id=20 |
Specify each port to be as an access port, enable secure VLAN mode on each port and on the switch1-cpu port:
| Code Block | ||
|---|---|---|
| ||
/interface ethernet switch port set ether2 default-vlan-id=10 vlan-header=always-strip vlan-mode=secure set ether3 default-vlan-id=20 vlan-header=always-strip vlan-mode=secure set switch1-cpu vlan-mode=secure |
...
| Note |
|---|
On QCA8337 and Atheros8327 switch chips, a default |
If your device has a switch rule table, then you can limit access between VLANs on a hardware level. As soon as you add an IP address on the VLAN interface you enable inter-VLAN routing, but this can be limited on a hardware level while preserving DHCP Server and other router-related services. To do so, use these ACL rules. With this type of configuration, you can achieve isolated port groups using VLANs.
| Code Block | ||
|---|---|---|
| ||
/interface ethernet switch rule add dst-address=192.168.20.0/24 new-dst-ports="" ports=ether2 switch=switch1 add dst-address=192.168.10.0/24 new-dst-ports="" ports=ether3 switch=switch1 |
...