Introduction
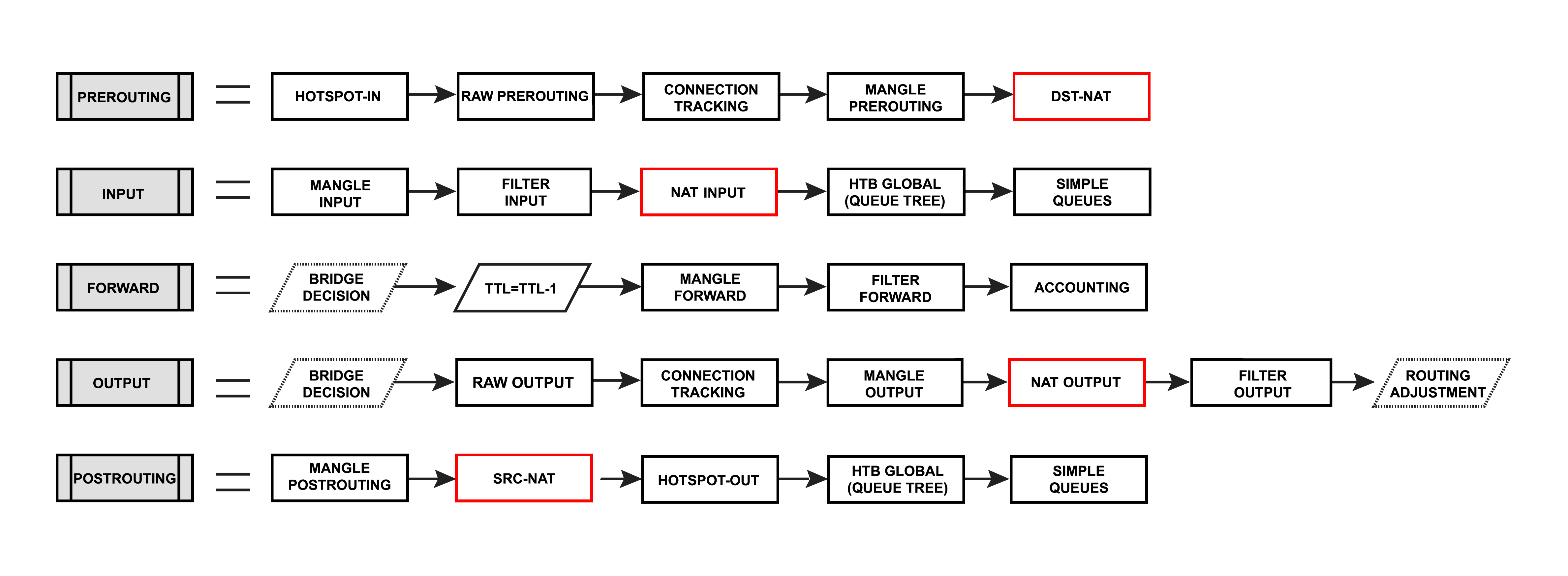
Network Address Translation is an Internet standard that allows hosts on local area networks to use one set of IP addresses for internal communications and another set of IP addresses for external communications. A LAN that uses NAT is ascribed as a natted network. For NAT to function, there should be a NAT gateway in each natted network. The NAT gateway (NAT router) performs IP address rewriting on the way packet travel from/to LAN.
Nat matches only the first packet of the connection, connection tracking remembers the action and performs on all other packets belonging to the same connection.
Whenever NAT rules are changed or added, the connection tracking table should be cleared otherwise NAT rules may seem to be not functioning correctly until connection entry expires.
Types of NAT:
- source NAT or srcnat. This type of NAT is performed on packets that are originated from a natted network. A NAT router replaces the private source address of an IP packet with a new public IP address as it travels through the router. A reverse operation is applied to the reply packets traveling in the other direction.
- destination NAT or dstnat. This type of NAT is performed on packets that are destined for the natted network. It is most commonly used to make hosts on a private network to be accessible from the Internet. A NAT router performing dstnat replaces the destination IP address of an IP packet as it travels through the router towards a private network.
Source NAT
For example, the basic rule to hide local networks behind one public IP:
/ip firewall nat add chain=srcnat action=src-nat to-address=1.1.1.1 out-interface=Public
As you can see from the example, we are using the srcnat chain because we want to manipulate the source information. By specifying out interface we ensure that the source will be modified only for those packets that leave a specific interface, in our case, it is an interface named "Public", and the last action is to src-nat - change the source address of the packet to global address configured on "Public" interface.
Masquerade
/ip firewall nat add chain=srcnat action=masquerade out-interface=Public
NAT action masquerade is a unique subversion of srcnat. It was designed for specific use in situations when public IP can randomly change, for example, DHCP server change assigned IP or PPPoE tunnel after disconnect gets different IP, in short - when public IP is dynamic.
Every time when interface disconnects and/or its IP address changes, the router will clear all masqueraded connection tracking entries related to the interface, this way improving system recovery time after public IP change.
Unfortunately, this can lead to some issues with unstable links when the connection gets routed over different links after the primary link goes down. In such a scenario following things can happen:
- on disconnect, all related connection tracking entries are purged;
- next packet from every purged (previously masqueraded) connection will come into firewall as new, and, if a primary interface is not back, a packet will be routed out via alternative route (if you have any) thus creating a new masqueraded connection;
- the primary link comes back, routing is restored over the primary link, so packets that belong to existing connections are sent over primary interface without being masqueraded, that way leaking local IPs to a public network.
To work around this situation blackhole route can be created as an alternative to the route that might disappear on disconnect.
If srcnat is used instead of masquerade, connection tracking entries remain and connections can simply resume after a link failure.
Hosts behind a NAT-enabled router do not have true end-to-end connectivity. Therefore some Internet protocols might not work in scenarios with NAT. Services that require the initiation of TCP connection from outside the private network or stateless protocols such as UDP, can be disrupted. Moreover, some protocols are inherently incompatible with NAT, a bold example is AH protocol from the IPsec suite.
To overcome these limitations RouterOS includes a number of so-called NAT helpers, that enable NAT traversal for various protocols.
Destination NAT
Let's see an opposite example where we want to change the destination address or perform port mapping:
/ip firewall nat add chain=dstnatdst-port=1234action=dst-natprotocol=tcpto-address=192.168.88.2to-port=12340What this rule does is, when an incoming connection requests TCP port 1234, it uses the dst-nat action and redirect it to local address 192.168.88.2 and the port 12340. In this example, we chose to specify ports to illustrate how traffic can be mapped from one port to another. If you do not specify a to-port parameter, then the destination port inside the packet is not changed.
NAT examples
Destination NAT
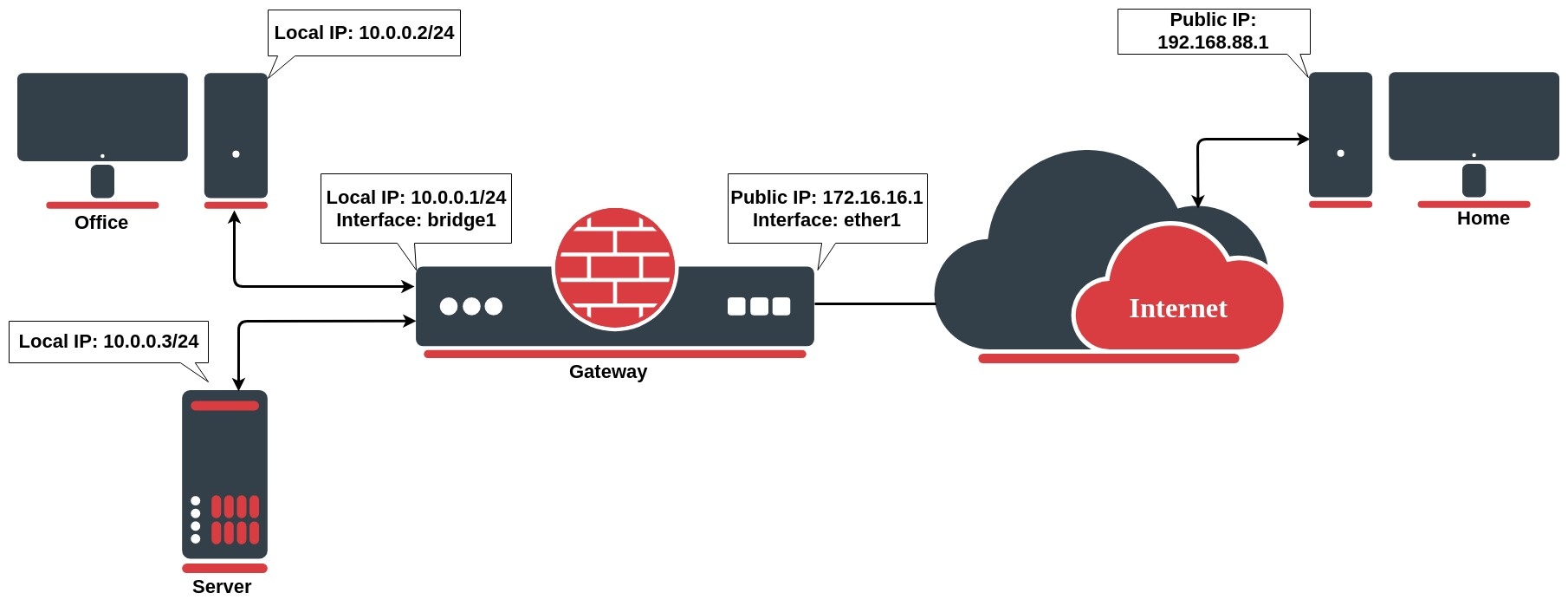
Network address translation works by modifying network address information in the packets IP header. Let`s take a look at the common setup where a network administrator wants to access an office server from the internet.
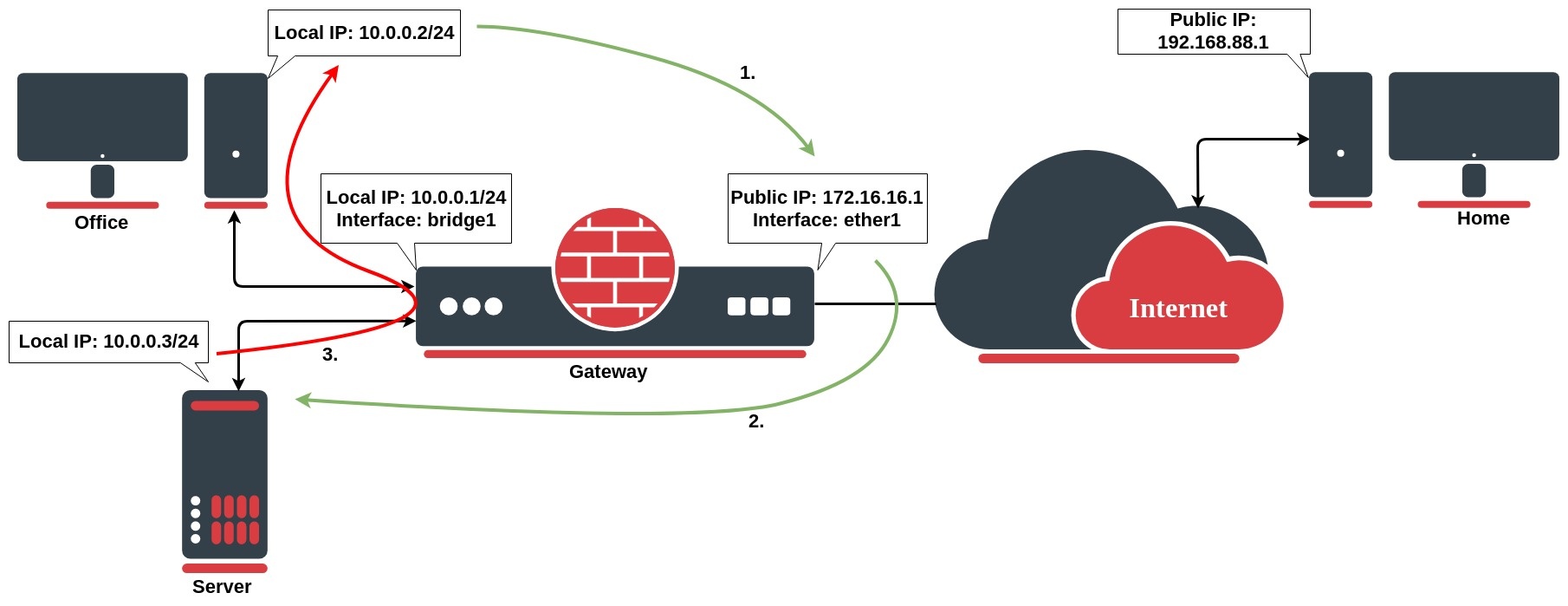
We want to allow connections from the internet to the office server whose local IP is 10.0.0.3. In this case, we have to configure a destination address translation rule on the office gateway router:
/ip firewall nat add chain=dstnat action=dst-nat dst-address=172.16.16.1 dst-port=22 to-addresses=10.0.0.3 protocol=tcp
The rule above translates: when an incoming connection requests TCP port 22 with destination address 172.16.16.1, use the dst-nat action and depart packets to the device with local IP address 10.0.0.3 and port 22.
To allow access only from the PC at home, we can improve our dst-nat rule with "src-address=192.168.88.1" which is a Home`s PC public IP address. It is also considered to be more secure.
To allow an internal server to initiate connections to the outer networks having its source address 10.0.0.3 translated to 172.16.16.1 you have to configure the following source-nat rule:
/ip firewall nat add chain=srcnat src-address=10.0.0.3 action=src-nat to-addresses=172.16.16.1
Source NAT
If you want to hide your local devices behind your public IP address received from ISP, you should configure the source network address translation (masquerading) feature of the MikroTik router.
Let`s assume you want to hide both office computer and server behind the public IP 172.16.16.1, the rule will look like the following one:
/ip firewall nat add chain=srcnat src-address=10.0.0.0/24 action=src-nat to-addresses=172.16.16.1 out-interface=WAN
Now your ISP will see all the requests coming with IP 172.16.16.1 and they will not see your LAN network IP addresses.
Masquerade
Firewall NAT action=masquerade is a unique subversion of action=srcnat, it was designed for specific use in situations when public IP can randomly change, for example, DHCP-server changes it, or PPPoE tunnel after disconnect gets different IP, in short - when public IP is dynamic. Every time the interface disconnects and/or its IP address changes, the router will clear all masqueraded connection tracking entries that send a packet out of that interface. This improves recovery time after public IP address changes.
Unfortunately, this can lead to some issues when action=masquerade is used in setups with unstable connections/links that get routed over the different links when the primary is down. In such a scenario following things can happen:
- on disconnect, all related connection tracking entries are purged;
- next packet from every purged (previously masqueraded) connection will come into firewall as connection-state=new, and, if a primary interface is not back, a packet will be routed out via alternative route (if you have any) thus creating a new connection;
- the primary link comes back, routing is restored over the primary link, so packets that belong to existing connections are sent over the primary interface without being masqueraded leaking local IPs to a public network. You can work around this by creating a blackhole route as an alternative to a route that might disappear on disconnect.
When action=srcnat is used instead, connection tracking entries remain and connections can simply resume.
/ip firewall nat add chain=srcnat src-address=10.0.0.0/24 action=masquarade out-interface=WAN
Though Source NAT and masquerading perform the same fundamental function: mapping one address space into another one, the details differ slightly. Most noticeably, masquerading chooses the source IP address for the outbound packet from the IP bound to the interface through which the packet will exit.
Hairpin NAT
Hairpin network address translation (NAT Loopback) is where the device on the LAN is able to access another machine on the LAN via the public IP address of the gateway router.
In the following example gateway router consist of dst-nat configuration rule:
/ip firewall nat add chain=dstnat action=dst-nat dst-address=172.16.16.1 dst-port=443 to-addresses=10.0.0.3 to-ports=443 protocol=tcp
When a customer from the PC at home establishes a connection to the webserver, the router performs NAT as configured:
- the client sends a packet with a source IP address of 192.168.88.1 to a destination IP address of 172.16.16.1 on port 443 to request some web resource;
- the router destination NAT`s the packet to 10.0.0.3 and replaces the destination IP address in the packet accordingly. The source IP address stays the same: 192.168.88.1;
- the server replies to the client's request and the reply packet have a source IP address of 10.0.0.3 and a destination IP address of 192.168.88.1.
- the router determines that the packet is part of a previous connection and undoes the destination NAT, and puts the original destination IP address into the source IP address field. The destination IP address is 192.168.88.1, and the source IP address is 172.16.16.1;
- The client receives the reply packet it expects, and the connection is established;
The issue occurs, when a client on the same internal network as the webserver requests a connection to the web server's public IP address, the connection breaks:
- the client sends a packet with a source IP address of 10.0.0.2 to a destination IP address of 172.16.16.1 on port 443 to request some web resource;
- the router destination NATs the packet to 10.0.0.3 and replaces the destination IP address in the packet accordingly. The source IP address stays the same: 10.0.0.2;
- the server replies to the client's request. However, the source IP address of the request is on the same subnet as the webserver. The web server does not send the reply back to the router but sends it back directly to 10.0.0.2 with a source IP address in the reply of 10.0.0.3;
- The client receives the reply packet, but it discards it because it expects a packet back from 172.16.16.1, and not from 10.0.0.3;
To resolve this issue, we will configure the src-nat rule as follows:
/ip firewall nat add action=masquerade chain=srcnat dst-address=10.0.0.3 out-interface=LAN protocol=tcp src-address=10.0.0.0/24
After configured rule above:
- the client sends a packet with a source IP address of 10.0.0.2 to a destination IP address of 172.16.16.1 on port 443 to request some web resource;
- the router destination NATs the packet to 10.0.0.3 and replaces the destination IP address in the packet accordingly. It also source NATs the packet and replaces the source IP address in the packet with the IP address on its LAN interface. The destination IP address is 10.0.0.3, and the source IP address is 10.0.0.1;
- the web server replies to the request and sends the reply with a source IP address of 10.0.0.3 back to the router's LAN interface IP address of 10.0.0.1;
- the router determines that the packet is part of a previous connection and undoes both the source and destination NAT, and puts the original destination IP address of 1.1.1.1 into the source IP address field, and the original source IP address of 172.16.16.1 into the destination IP address field;