...
Introduction
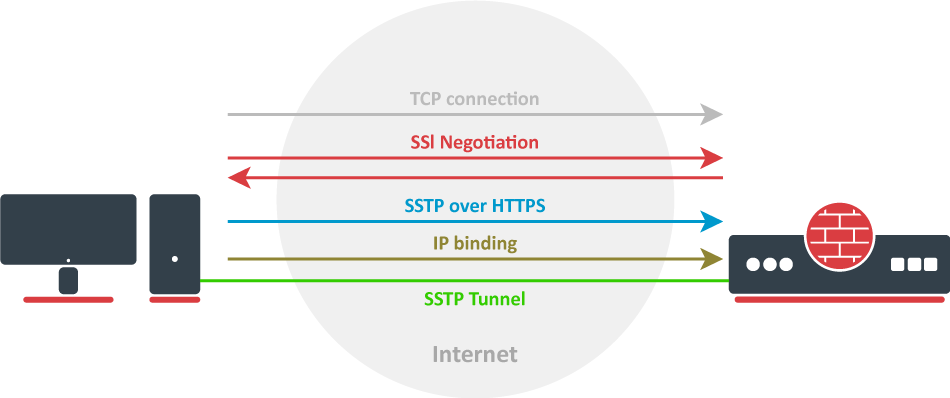
Let`s take a look at the SSTP connection mechanism:
- A TCP connection is established from client to server (by default on port 443);
- SSL validates the server certificate. If a certificate is valid, a connection is established otherwise the connection is turned down. (But see note below);
- The client sends SSTP control packets within the HTTPS session which establishes the SSTP state machine on both sides;
- PPP negotiation over SSTP. The client authenticates to the server and binds IP addresses to the SSTP interface;
SSTP tunnel is now established and packet encapsulation can begin;
| Note |
|---|
Starting from v5.0beta2 SSTP does not require certificates to operate and can use any available authentication type. This feature will work only between two MikroTik routers, as it is not in accordance with Microsoft standards. Otherwise to establish secure tunnels mschap authentication and client/server certificates from the same chain should be used. |
| Note |
|---|
TLS SNI support has been added starting with 7.15beta10 version, Extension will be added to client hello packets if "Add SNI" checkbox is checked or set in CLI: interface/sstp-client/set add-sni=yes |
Certificates
To set up a secure SSTP tunnel, certificates are required. On the server, authentication is done only by username and password, but on the client - the server is authenticated using a server certificate. It is also used by the client to cryptographically bind SSL and PPP authentication, meaning - the clients send a special value over SSTP connection to the server, this value is derived from the key data that is generated during PPP authentication and server certificate, this allows the server to check if both channels are secure.
...