Table of Contents
...
Overview
CAPsMAN allows to apply applying wireless settings to multiple MikroTik AP devices from a central configuration interface.
More specifically, the Controlled Access Point system Manager (CAPsMAN) allows centralization of wireless network management and if necessary, data processing. When using the CAPsMAN feature, the network will consist of a number of 'Controlled Access Points' (CAP) that provide wireless connectivity and a 'system Manager' (CAPsMAN) that manages the configuration of the APs, it also takes care of client authentication and optionally, data forwarding.
When a CAP is controlled by CAPsMAN it only requires the minimum configuration required to allow it to establish a connection with CAPsMAN. Functions that were conventionally executed by an AP (like access control, client authentication) are now executed by CAPsMAN. The CAP device now only has to provide the wireless link layer encryption/decryption.
Depending on the configuration, data is either forwarded to CAPsMAN for centralized processing (default) or forwarded locally at the CAP itself (local forwarding mode).
...
...
Starting from RouterOS v6.22rc7 a different CAPsMAN implementation is used, it is not compatible with older versions
Requirements
- Any RouterOS device can be a controlled wireless access point (CAP) as long as it has at least a Level 4 RouterOS license
- CAPsMAN server can be installed on any RouterOS device, even if the device itself does not have a wireless interface
- Unlimited CAPs (access points) supported by CAPsMAN
- 32 Radios per CAP maximum
- 32 Virtual interfaces per master radio interface maximum
- Not possible to use Nv2 and NStreme proprietary protocols
...
Simple setup of a CAPsMAN system
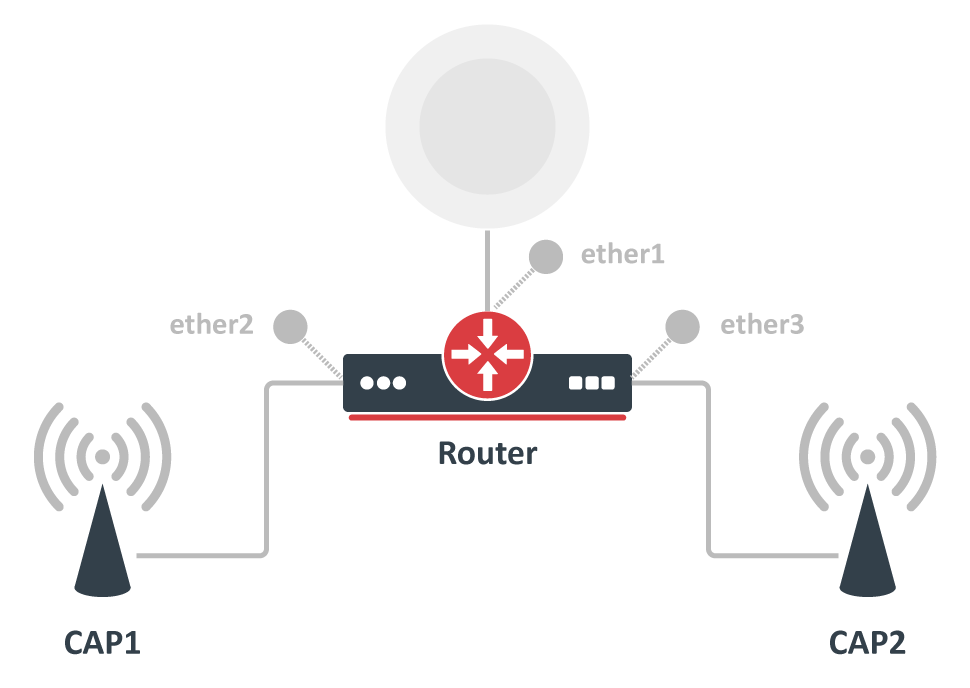
Before deep-diving into the details of CAPsMAN operation, let us quickly illustrate how to set up the most basic system where you have a MikroTik router that manages two MikroTik AP devices. The benefit of CAPsMAN is that the CAP units don't need to be configured, all settings are done in the CAPsMAN server.
...
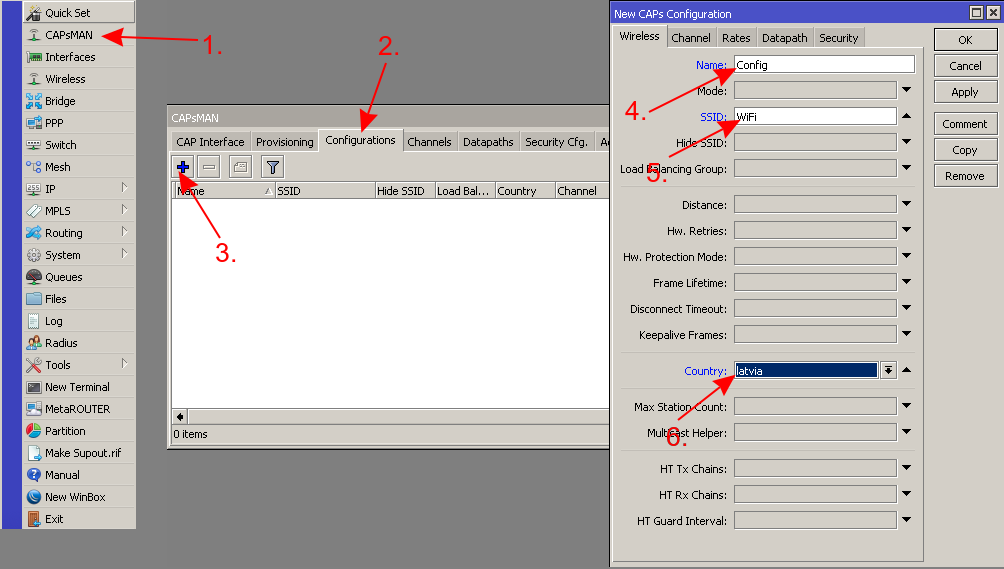
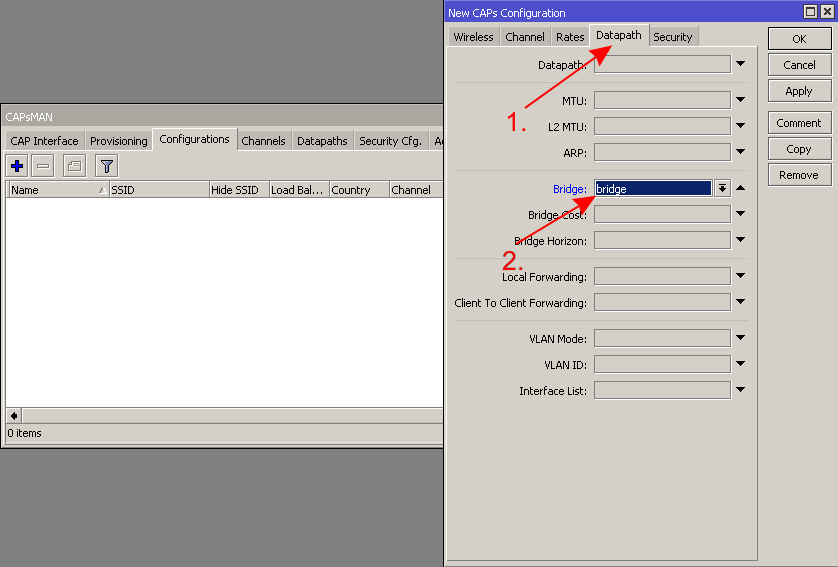
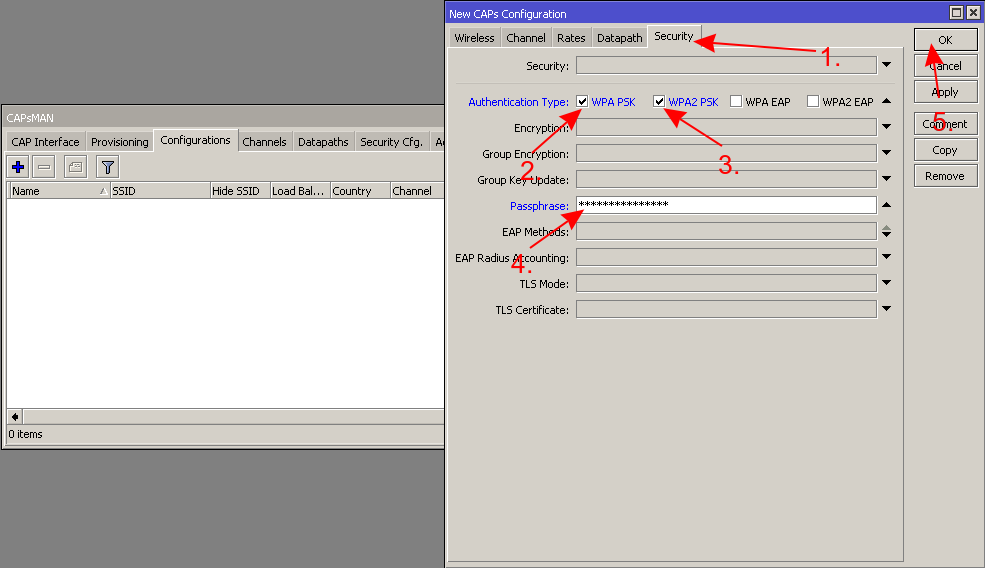
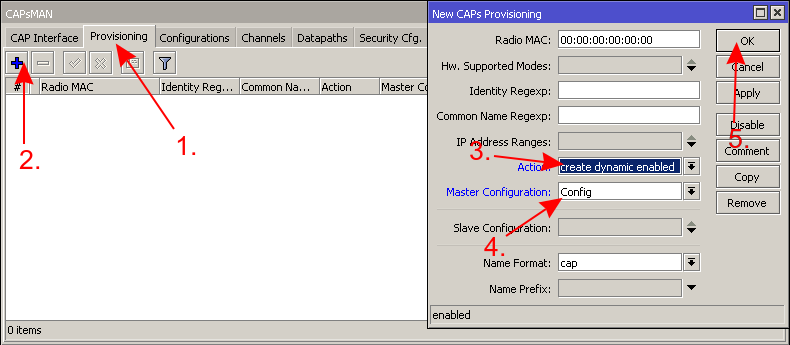
In the central device, which will be your CAPsMAN server, create a new "Configuration" template with only the basic settings (network name, country, the local LAN bridge interface, the wireless password):
1. 2. 3.
Then create a new "Provisioning" rule, which will assign the created configuration template to the CAP devices:
4.
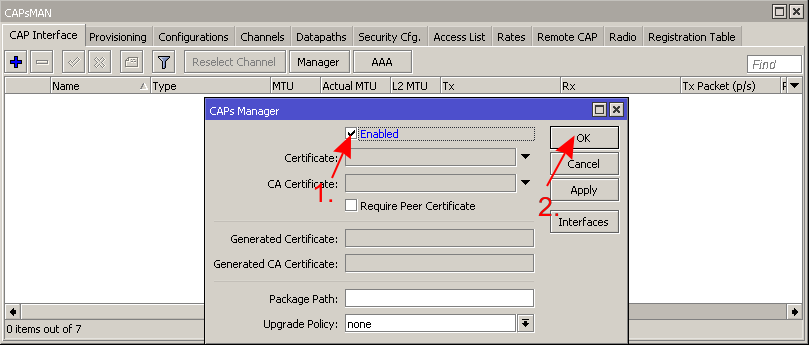
All that remains to do on the CAPsMAN, is to enable it:
5.
Most MikroTik AP devices already support CAP mode out of the box, all you need to do, is make sure they are on the same network as your CAPsMAN, and then boot them up, while holding the reset button.
...
The device will now show up in the CAPsMAN "Remote CAP" menu and will be "provisioned" with the configuration template, as per the provisioning settings. For more details on how to manually adjust all settings, keep reading this document.
...
CAP to CAPsMAN Connection
For the CAPsMAN system to function and provide wireless connectivity, a CAP must establish management connection with CAPsMAN. A management connection can be established using MAC or IP layer protocols and is secured using 'DTLS'.
...
If the CAPsMAN or CAP gets disconnected from the network, the loss of connection between CAP and CAPsMAN will be detected in approximately 10-20 seconds.
CAP Auto Locking to CAPsMAN
CAP can be configured to automatically lock to a particular CAPsMAN server. Locking is implemented by recording certificate CommonName of CAPsMAN that CAP is locked to and checking this CommonName for all subsequent connections. As this feature is implemented using certificate CommonName, use of certificates is mandatory for locking to work.
...
Note that CAP can be manually "locked" to CAPsMAN by setting caps-man-certificate-common-names.
Auto Certificates
| Anchor | ||||
|---|---|---|---|---|
|
To simplify CAPsMAN and CAP configuration when certificates are required (e.g. for automatic locking feature), CAPsMAN can be configured to generate necessary certificates automatically and CAP can be configured to request certificate from CAPsMAN.
...
On subsequent connections to CAPsMAN, CAP will use generated certificate.
...
CAP Configuration
When an AP is configured to be controlled by CAPsMAN, configuration of the managed wireless interfaces on the AP is ignored (exceptions: antenna-gain,antenna-mode). Instead, AP accepts configuration for the managed interfaces from CAPsMAN.
| Note |
|---|
The CAP wireless interfaces that are managed by CAPsMAN and whose traffic is being forwarded to CAPsMAN (ie. they are not in local forwarding mode), are shown as disabled, with the note Managed by CAPsMAN. Those interfaces that are in local forwarding mode (traffic is locally managed by CAP, and only management is done by CAPsMAN) are not shown disabled, but the note Managed by CAPsMAN is shown |
CAP behaviour behavior of AP is configured in /interface wireless cap menu. It contains the following settings:
...
From there you can:
...
- Disable or enable CAP feature on the device
...
- Set list of
...
- wireless interfaces to be controlled by Manager
...
- Set list of interfaces over which CAP should attempt to discover Manager
...
- Set list of
...
- Manager IP addresses that CAP will attempt to contact during discovery
...
- Set list of Manager names that CAP will attempt to connect
...
- Set list
...
- of Manager certificate CommonNames that CAP will connect to
...
- Set bridge
...
- to which interfaces should be added when local forwarding mode is used
...
CAPsMAN Configuration Concepts
Each wireless interface on a CAP that is under CAPsMAN control appears as a virtual interface on the CAPsMAN. Each wireless interface on a CAP that is under CAPsMAN control appears as a virtual interface on the CAPsMAN. This provides maximum flexibility in data forwarding control using regular RouterOS features, such as routing, bridging, firewall, etc.CAPsMAN Configuration Concepts
Many wireless interface settings are able to be grouped together into named groups ('profiles') that simplifies the reuse of configuration - for example, common configuration settings can be configured in a 'configuration profile' and multiple interfaces can then refer to that profile. At the same time any profile setting can be overridden directly in an interface configuration for maximum flexibility.
...
Interfaces on CAPsMAN can be static or dynamic. Static interfaces are stored in RouterOS configuration and will persist across reboots. Dynamic interfaces exist only while a particular CAP is connected to CAPsMAN.
CAPsMAN Global Configuration
Settings to enable CAPsMAN functionality are found in /caps-man manager menu:
| Property | Description |
|---|---|
| enabled (yes | no; Default: no) | Disable or enable CAPsMAN functionality |
| certificate (auto | certificate name | none; Default: none) | Device certificate |
| ca-certificate (auto | certificate name | none; Default: none) | Device CA certificate |
| require-peer-certificate (yes | no; Default: no) | Require all connecting CAPs to have a valid certificate |
| package-path (string |; Default: ) | Folder location for the RouterOS packages. For example, use "/upgrade" to specify the upgrade folder from the files section. If empty string is set, CAPsMAN can use built-in RouterOS packages, note that in this case only CAPs with the same architecture as CAPsMAN will be upgraded. |
| upgrade-policy (none | require-same-version | suggest-same-upgrade; Default: none) | Upgrade policy options
|
Radio Provisioning
CAPsMAN distinguishes between CAPs based on an identifier. The identifier is generated based on the following rules:
...
[admin@CM] > caps-man remote-cap provision 0
Interface Configuration
CAPsMAN interfaces are managed in /caps-man interface menu:
[admin@CM] > /caps-man interface print Flags: M - master, D - dynamic, B - bound, X - disabled, I - inactive, R - running # NAME RADIO-MAC MASTER-INTERFACE 0 M BR cap2 00:0C:42:1B:4E:F5 none 1 B cap3 00:00:00:00:00:00 cap2
Master Configuration Profiles
Configuration profiles permit pre-defined 'top level' master settings to be applied to CAP radios being provisioned.
...
| Property | Description |
|---|---|
| channel (list; Default: ) | User defined list taken from Channel names (/caps-man channels) |
| channel.band (2ghz-b | 2ghz-b/g | 2ghz-b/g/n | 2ghz-onlyg | 2ghz-onlyn | 5ghz-a | 5ghz-a/n | 5ghz-onlyn | 5ghz-a/n/ac | 5ghz-only-ac; Default: ) | Defines set of used channels. |
| channel.control-channel-width (40mhz-turbo | 20mhz | 10mhz | 5mhz; Default: ) | Defines set of used channel widths. |
| channel.extension-channel (Ce | Ceee | eC | eCee | eeCe | eeeC | xx | xxxx | disabled; Default: ) | Extension channel configuration. (E.g. Ce = extension channel is above Control channel, eC = extension channel is below Control channel) |
| channel.frequency (integer [0..4294967295]; Default: ) | Channel frequency value in MHz on which AP will operate. If left blank, CAPsMAN will automatically determine the best frequency that is least occupied. |
| channel.reselect-interval (time [00:00:00]; Default [00:00:00..00:00:00]; Default: ) | Interval The interval after which the least occupied frequency is chosen, can be defined as a random interval, ex. as "30m..60m". Works only if channel.frequency is left blank. |
| channel.save-selected (yes | no; Default: no) | If channel frequency is chosen automatically and channel.reselect-interval is used, then saves the last picked frequency. |
| channel.secondary-frequency (integer [0..4294967295]; Default: auto) | Specifies the second frequency that will be used for 80+80MHz configuration. Set it to Disabled in order to disable 80+80MHz capability. |
| channel.skip-dfs-channels (yes | no; Default: no) | If channel.frequency is left blank, the selection will skip DFS channels |
| channel.tx-power (integer [-30..40]; Default: ) | TX Power for CAP interface (for the whole interface not for individual chains) in dBm. It is not possible to set higher than allowed by country regulations or interface. By default max allowed by country or interface is used. |
| channel.width (; Default: ) | Sets Channel Width in MHz. |
| comment (string; Default: ) | Short description of the Configuration profile |
| country (name of the country | no_country_set; Default: no_country_set) | Limits available bands, frequencies and maximum transmit power for each frequency. Also specifies default value of scan-list. Value no_country_set is an FCC compliant set of channels. |
| datapath (list; Default: ) | User defined list taken from Datapath names (/caps-man datapath) |
| datapath.bridge (list; Default: ) | Bridge to which particular interface should be automatically added as port |
| datapath.bridge-cost (integer [01..4294967295200000000]; Default: ) | bridge port cost to use when adding as bridge port |
| datapath.bridge-horizon (integer [0..4294967295]; Default: ) | bridge horizon to use when adding as bridge port |
| datapath.client-to-client-forwarding (yes | no; Default: no) | controls if client-to-client forwarding between wireless clients connected to interface should be allowed, in local forwarding mode this function is performed by CAP, otherwise it is performed by CAPsMAN |
| datapath.interface-list (; Default: ) | |
| datapath.l2mtu (; Default: ) | set Layer2 MTU size |
| datapath.local-forwarding (yes | no; Default: no) | controls forwarding mode |
| datapath.mtu (; Default: ) | set MTU size |
| datapath.openflow-switch (; Default: ) | OpenFlow switch port (when enabled) to add interface to |
| datapath.vlan-id (integer [1..4095]; Default: ) | VLAN ID to assign to interface if vlan-mode enables use of VLAN tagging |
| datapath.vlan-mode (use-service-tag | use-tag; Default: ) | Enables and specifies the type of VLAN tag to be assigned to the interface (causes all received data to get tagged with VLAN tag and allows the interface to only send out data tagged with given tag) |
| disconnect-timeout (; Default: ) | |
| distance (; Default: ) | |
| frame-lifetime (; Default: ) | |
| guard-interval (any | long; Default: any) | Whether to allow the use of short guard interval (refer to 802.11n MCS specification to see how this may affect throughput). "any" will use either short or long, depending on data rate, "long" will use long only. |
| hide-ssid (yes | no; Default: ) |
|
| hw-protection-mode (; Default: ) | |
| hw-retries (; Default: ) | |
| installation (any | indoor | outdoor; Default: any) | |
| keepalive-frames (enabled | disabled; Default: enabled) | |
| load-balancing-group (string; Default: ) | Tags the interface to the load balancing group. For a client to connect to interface in this group, the interface should have the same number of already connected clients as all other interfaces in the group or smaller. Useful in setups where ranges of CAPs mostly overlap. |
| max-sta-count (integer [1..2007]; Default: ) | Maximum number of associated clients. |
| mode (; Default: ap) | Set operational mode. Only ap currently supported. |
| multicast-helper (default | disabled | full; Default: default) | When set to full multicast packets will be sent with unicast destination MAC address, resolving multicast problem on a wireless link. This option should be enabled only on the access point, clients should be configured in station-bridge mode. Available starting from v5.15.
|
| name (string; Default: ) | Descriptive name for the Configuration Profile |
| rates (; Default: ) | User defined list taken from Rates names (/caps-man rates) |
| rates.basic (1Mbps | 2Mbps | 5.5Mbps | 6Mbps | 11Mbps | 11Mbps | 12Mbps | 18Mbps | 24Mbps | 36Mbps | 48Mbps | 54Mbps; Default: ) | |
| rates.supported (1Mbps | 2Mbps | 5.5Mbps | 6Mbps | 11Mbps | 11Mbps | 12Mbps | 18Mbps | 24Mbps | 36Mbps | 48Mbps | 54Mbps; Default: ) | |
| rates.ht-basic-mcs (list of (mcs-0 | mcs-1 | mcs-2 | mcs-3 | mcs-4 | mcs-5 | mcs-6 | mcs-7 | mcs-8 | mcs-9 | mcs-10 | mcs-11 | mcs-12 | mcs-13 | mcs-14 | mcs-15 | mcs-16 | mcs-17 | mcs-18 | mcs-19 | mcs-20 | mcs-21 | mcs-22 | mcs-23); Default: mcs-0; mcs-1; mcs-2; mcs-3; mcs-4; mcs-5; mcs-6; mcs-7) | Modulation and Coding Schemes that every connecting client must support. Refer to 802.11n for MCS specification. |
| rates.ht-supported-mcs (list of (mcs-0 | mcs-1 | mcs-2 | mcs-3 | mcs-4 | mcs-5 | mcs-6 | mcs-7 | mcs-8 | mcs-9 | mcs-10 | mcs-11 | mcs-12 | mcs-13 | mcs-14 | mcs-15 | mcs-16 | mcs-17 | mcs-18 | mcs-19 | mcs-20 | mcs-21 | mcs-22 | mcs-23); Default: mcs-0; mcs-1; mcs-2; mcs-3; mcs-4; mcs-5; mcs-6; mcs-7; mcs-8; mcs-9; mcs-10; mcs-11; mcs-12; mcs-13; mcs-14; mcs-15; mcs-16; mcs-17; mcs-18; mcs-19; mcs-20; mcs-21; mcs-22; mcs-23) | Modulation and Coding Schemes that this device advertises as supported. Refer to 802.11n for MCS specification. |
| rates.vht-basic-mcs (none | MCS 0-7 | MCS 0-8 | MCS 0-9; Default: none) | Modulation and Coding Schemes that every connecting client must support. Refer to 802.11ac for MCS specification. You can set MCS interval for each of Spatial Stream
|
| rates.vht-supported-mcs (none | MCS 0-7 | MCS 0-8 | MCS 0-9; Default: none) | Modulation and Coding Schemes that this device advertises as supported. Refer to 802.11ac for MCS specification. You can set MCS interval for each of Spatial Stream
|
| rx-chains (list of integer [0..2]; Default: 0) | Which antennas to use for receive. |
| security (string; Default: none) | Name of security configuration from /caps-man security |
| security.authentication-types (list of string; Default: none) | Specify the type of Authentication from wpa-psk, wpa2-psk, wpa-eap or wpa2-eap |
| security.disable-pmkid (; Default: ) | |
| security.eap-methods (eap-tls | passthrough; Default: none) |
|
| security.eap-radius-accounting (; Default: ) | |
| security.encryption (aes-ccm | tkip; Default: aes-ccm) | Set type of unicast encryption algorithm used |
| security.group-encryption (aes-ccm | tkip; Default: aes-ccm) | Access Point advertises one of these ciphers, multiple values can be selected. Access Point uses it to encrypt all broadcast and multicast frames. Client attempts connection only to Access Points that use one of the specified group ciphers.
|
| security.group-key-update (time: 30s..1h; Default: 5m) | Controls how often Access Point updates the group key. This key is used to encrypt all broadcast and multicast frames. property only has effect for Access Points. |
| security.passphrase (string; Default: ) | WPA or WPA2 pre-shared key |
| security.tls-certificate (none | name; Default: ) | Access Point always needs a certificate when configured when security.tls-mode is set to verify-certificate, or is set to dont-verify-certificate. |
| security.tls-mode (verify-certificate | dont-verify-certificate | no-certificates; Default: ) | This property has effect only when security.eap-methods contains eap-tls.
|
| ssid (string (0..32 chars); Default: ) | SSID (service set identifier) is a name broadcast in the beacons that identifies wireless network. |
| tx-chains (list of integer [0..2]; Default: 0) | Which antennas to use for transmit. |
Channel Groups
Channel group settings allows for the configuration of lists of radio channel related settings, such as radio band, frequency, Tx Power extension channel and width.
...
| Property | Description |
|---|---|
| band (2ghz-b | 2ghz-b/g | 2ghz-b/g/n | 2ghz-onlyg | 2ghz-onlyn | 5ghz-a | 5ghz-a/n | 5ghz-onlyn; Default: ) | Define operational radio frequency band and mode taken from hardware capability of wireless card |
| comment (string; Default: ) | Short description of the Channel Group profile |
| extension-channel (Ce | Ceee | eC | eCee | eeCe | eeeC | disabled; Default: ) | Extension channel configuration. (E.g. Ce = extension channel is above Control channel, eC = extension channel is below Control channel) |
| frequency (integer [0..4294967295]; Default: ) | Channel frequency value in MHz on which AP will operate. |
| name (string; Default: ) | Descriptive name for the Channel Group Profile |
| tx-power (integer [-30..40]; Default: ) | TX Power for CAP interface (for the whole interface not for individual chains) in dBm. It is not possible to set higher than allowed by country regulations or interface. By default max allowed by country or interface is used. |
| width (; Default: ) | Sets Channel Width in MHz. (E.g. 20, 40) |
| save-selected (; Default: yes) | Saves selected channel for the CAP Radio - will select this channel after the CAP reconnects to CAPsMAN and use it till the channel Re-optimize is done for this CAP. |
Datapath Configuration
Datapath settings control data forwarding related aspects. On CAPsMAN datapath settings are configured in datapath profile menu /caps-man datapath or directly in a configuration profile or interface menu as settings with datapath. prefix.
...
- bridge -- bridge interface to add interface to, as a bridge port, when enabled
- bridge-cost -- bridge port cost to use when adding as bridge port
- bridge-horizon -- bridge horizon to use when adding as bridge port
- client-to-client-forwarding -- controls if client-to-client forwarding between wireless clients connected to interface should be allowed, in local forwarding mode this function is performed by CAP, otherwise it is performed by CAPsMAN.
- local-forwarding -- controls forwarding mode
- openflow-switch -- OpenFlow switch to add interface to, as port when enabled
- vlan-id -- VLAN ID to assign to interface if vlan-mode enables use of VLAN tagging
- vlan-mode -- VLAN tagging mode specifies if VLAN tag should be assigned to interface (causes all received data to get tagged with VLAN tag and allows interface to only send out data tagged with given tag)
Local Forwarding Mode
In this mode wireless interface on CAP behaves as a normal interface and takes part in normal data forwarding. Wireless interface will accept/pass data to networking stack on CAP. CAPsMAN will not participate in data forwarding and will not process any of data frames, it will only control interface configuration and client association process.
...
To facilitate data forwarding configuration, CAP can be configured with bridge to which interfaces are automatically added as ports when interfaces are enabled by CAPsMAN. This can be done in /interface wireless cap menu.
Manager Forwarding Mode
In this mode CAP sends all data received over wireless to CAPsMAN and only sends out over wireless, data received from CAPsMAN. CAPsMAN has full control over data forwarding including client-to-client forwarding. Wireless interface on CAP is disabled and does not participate in networking:
...
Virtual-AP interfaces are also created as 'disabled' and do not take part in data forwarding on CAP.
Access List
Access list on CAPsMAN is an ordered list of rules that is used to allow/deny clients to connect to any CAP under CAPsMAN control. When client attempts to connect to a CAP that is controlled by CAPsMAN, CAP forwards that request to CAPsMAN. As a part of registration process, CAPsMAN consults access list to determine if client should be allowed to connect. The default behaviour of the access list is to allow connection.
...
- client matching parameters:
- address - MAC address of client (or, if mask is specified, only those parts will be checked as per the mask, so to match vendor D8 from "D8:1C:79:6E:1E:FE", simply enter a bogus entry, such as "D8:00:00:00:00" and then use the mask as per next line)
- mask - MAC address mask to apply when comparing client address. For example, use FF:00:00:00:00:00 to match only the first octet of the specified MAC address. In above example, regardless of entered MAC, it will match only first octet. Similarly, entering 00:00:00:00:FF will only match the last octet (FE) of a hypotetical MAC "D8:1C:79:6E:1E:FE"). So in the mac line, you could just enter 00:00:00:00:00:FE, if you would use such a mask.
- interface - optional interface to compare with interface to which client actually connects to
- time - time of day and days when rule matches
- signal-range - range in which client signal must fit for rule to match
- action parameter - specifies action to take when client matches:
- accept - accept client
- reject - reject client
- query-radius - query RADIUS server if particular client is allowed to connect
- connection parameters:
- ap-tx-limit - tx speed limit in direction to client
- client-tx-limit - tx speed limit in direction to AP (applies to RouterOS clients only)
- client-to-client-forwarding - specifies whether to allow forwarding data received from this client to other clients connected to the same interface
- private-passphrase - PSK passphrase to use for this client if some PSK authentication algorithm is used
- radius-accounting - specifies if RADIUS traffic accounting should be used if RADIUS authentication gets done for this client
- vlan-mode - VLAN tagging mode specifies if traffic coming from client should get tagged (and untagged when going to client).
- vlan-id - VLAN ID to use if doing VLAN tagging.
Registration Table
Registration table contains a list of clients that are connected to radios controlled by CAPsMAN and is available in /caps-man registration-table menu:
[admin@CM] /caps-man> registration-table print # INTERFACE MAC-ADDRESS UPTIME RX-SIGNAL 0 cap1 00:03:7F:48:CC:0B 1h38m9s210ms -36
Examples
Basic configuration with master and slave interface
Create security profile for WPA2 PSK, without specifying passphrase:
...
DHCP client this CAPsMAN IP will see in "/ip dhcp-client print detail"
Configuration with certificates
You would want to configure certificates in your CAPsMAN to use options as Require Peer Certificate and Lock To Caps Man. These options increase security and in some cases stability of your CAPsMAN network. CAPs won't connect to CAPsMAN without a specific certificate and vice versa.
Fast and easy configuration
This is a basic configuration for using certificates in your CAPsMAN setup. This example assumes that you already have basic configuration on your CAPsMAN and CAP. It is best to use this configuration in CAPsMAN networks which are not constantly growing. For more details read about CAP to CAPsMAN Connection.
...
/interface wireless cap set lock-to-caps-man=yes set caps-man-certificate-common-names=CAPsMAN-D4CA6D987C26
Manual certificates and issuing with SCEP
With this example, you can create your own certificates for CAPsMAN and take control over issuing certificates to CAPs. This configuration can be useful in big, growing CAPsMAN networks. Many segments of this example can be done differently depending on your situation and needs. At this point, some knowledge about Certificates and their application can be useful.
...