...
Linux (strongSwan) client configuration
Download the PKCS12 certificate bundle and move it to /etc/ipsec.d/private directory.
Add exported passphrase for the private key to /etc/ipsec.secrets file where "strongSwan_client.p12" is the file name and "1234567890" is the passphrase.
| Code Block |
|---|
|
: P12 strongSwan_client.p12 "1234567890" |
...
| Code Block |
|---|
|
$ ipsec restart
$ ipsec up ikev2 |
Basic L2TP/IPsec setup
This example demonstrates how to easily set up an L2TP/IPsec server on RouterOS for road warrior connections (works with Windows, Android, iOS, macOS, and other vendor L2TP/IPsec implementations).
RouterOS server configuration
The first step is to enable the L2TP server:
| Code Block |
|---|
|
/interface l2tp-server server
set enabled=yes use-ipsec=required ipsec-secret=mySecret default-profile=default |
use-ipsec is set to required to make sure that only IPsec encapsulated L2TP connections are accepted.
Now what it does is enables an L2TP server and creates a dynamic IPsec peer with a specified secret.
| Code Block |
|---|
|
[admin@MikroTik] /ip ipsec peer> print
0 D address=0.0.0.0/0 local-address=0.0.0.0 passive=yes port=500
auth-method=pre-shared-key secret="123" generate-policy=port-strict
exchange-mode=main-l2tp send-initial-contact=yes nat-traversal=yes
hash-algorithm=sha1 enc-algorithm=3des,aes-128,aes-192,aes-256
dh-group=modp1024 lifetime=1d dpd-interval=2m dpd-maximum-failures=5 |
| Note |
|---|
Care must be taken if static IPsec peer configuration exists. |
The next step is to create a VPN pool and add some users.
| Code Block |
|---|
|
/ip pool add name=vpn-pool range=192.168.99.2-192.168.99.100
/ppp profile
set default local-address=192.168.99.1 remote-address=vpn-pool
/ppp secret
add name=user1 password=123
add name=user2 password=234 |
Now the router is ready to accept L2TP/IPsec client connections.
RouterOS client configuration
For RouterOS to work as L2TP/IPsec client, it is as simple as adding a new L2TP client.
| Code Block |
|---|
|
/interface l2tp-client
add connect-to=1.1.1.1 disabled=no ipsec-secret=mySecret name=l2tp-out1 \
password=123 use-ipsec=yes user=user1 |
It will automatically create dynamic IPsec peer and policy configurations.
Site to Site GRE tunnel over IPsec (IKEv2) using DNS
This example explains how it is possible to establish a secure and encrypted GRE tunnel between two RouterOS devices when one or both sites do not have a static IP address. Before making this configuration possible, it is necessary to have a DNS name assigned to one of the devices which will act as a responder (server). For simplicity, we will use RouterOS built-in DDNS service IP/Cloud.
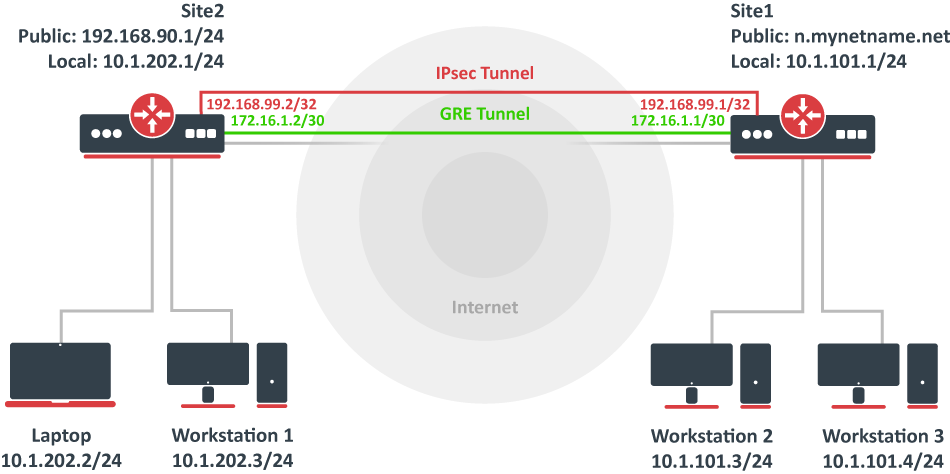 Image Added
Image Added
Site 1 (server) configuration
This is the side that will listen to incoming connections and act as a responder. We will use mode config to provide an IP address for the second site, but first, create a loopback (blank) bridge and assign an IP address to it that will be used later for GRE tunnel establishment.
| Code Block |
|---|
|
/interface bridge
add name=loopback
/ip address
add address=192.168.99.1 interface=loopback |
Continuing with the IPsec configuration, start off by creating a new Phase 1 profile and Phase 2 proposal entries using stronger or weaker encryption parameters that suit your needs. Note that this configuration example will listen to all incoming IKEv2 requests, meaning the profile configuration will be shared between all other configurations (e.g. RoadWarrior).
| Code Block |
|---|
|
/ip ipsec profile
add dh-group=ecp256,modp2048,modp1024 enc-algorithm=aes-256,aes-192,aes-128 name=ike2
/ip ipsec proposal
add auth-algorithms=null enc-algorithms=aes-128-gcm name=ike2-gre pfs-group=none |
Next, create a new mode config entry with responder=yes. This will provide an IP configuration for the other site as well as the host (loopback address) for policy generation.
| Code Block |
|---|
|
/ip ipsec mode-config
add address=192.168.99.2 address-prefix-length=32 name=ike2-gre split-include=192.168.99.1/32 system-dns=no |
It is advised to create a new policy group to separate this configuration from any existing or future IPsec configuration.
| Code Block |
|---|
|
/ip ipsec policy group
add name=ike2-gre |
Now it is time to set up a new policy template that will match the remote peers new dynamic address and the loopback address.
| Code Block |
|---|
|
/ip ipsec policy
add dst-address=192.168.99.2/32 group=ike2-gre proposal=ike2-gre src-address=192.168.99.1/32 template=yes |
The next step is to create a peer configuration that will listen to all IKEv2 requests. If you already have such an entry, you can skip this step.
| Code Block |
|---|
|
/ip ipsec peer
add exchange-mode=ike2 name=ike2 passive=yes profile=ike2 |
Lastly, set up an identity that will match our remote peer by pre-shared-key authentication with a specific secret.
| Code Block |
|---|
|
/ip ipsec identity
add generate-policy=port-strict mode-config=ike2-gre peer=ike2 policy-template-group=ike2-gre secret=test |
The server side is now configured and listening to all IKEv2 requests. Please make sure the firewall is not blocking UDP/4500 port.
The last step is to create the GRE interface itself. This can also be done later when an IPsec connection is established from the client-side.
| Code Block |
|---|
|
/interface gre
add local-address=192.168.99.1 name=gre-tunnel1 remote-address=192.168.99.2 |
Site 2 (client) configuration
Similarly to server configuration, start off by creating a new Phase 1 profile and Phase 2 proposal configurations. Since this site will be the initiator, we can use a more specific profile configuration to control which exact encryption parameters are used, just make sure they overlap with what is configured on the server-side.
| Code Block |
|---|
|
/ip ipsec profile
add dh-group=ecp256 enc-algorithm=aes-256 name=ike2-gre
/ip ipsec proposal
add auth-algorithms=null enc-algorithms=aes-128-gcm name=ike2-gre pfs-group=none |
Next, create a new mode config entry with responder=no. This will make sure the peer requests IP and split-network configuration from the server.
| Code Block |
|---|
|
/ip ipsec mode-config
add name=ike2-gre responder=no |
It is also advised to create a new policy group to separate this configuration from any existing or future IPsec configuration.
| Code Block |
|---|
|
/ip ipsec policy group
add name=ike2-gre |
Create a new policy template on the client-side as well.
| Code Block |
|---|
|
/ip ipsec policy
add dst-address=192.168.99.1/32 group=ike2-gre proposal=ike2-gre src-address=192.168.99.2/32 template=yes |
Move on to peer configuration. Now we can specify the DNS name for the server under the address parameter. Obviously, you can use an IP address as well.
| Code Block |
|---|
|
/ip ipsec peer
add address=n.mynetname.net exchange-mode=ike2 name=p1.ez profile=ike2-gre |
Lastly, create an identity for our newly created peers.
| Code Block |
|---|
|
/ip ipsec identity
add generate-policy=port-strict mode-config=ike2-gre peer=p1.ez policy-template-group=ike2-gre secret=test |
If everything was done properly, there should be a new dynamic policy present.
| Code Block |
|---|
|
/ip ipsec policy print
Flags: T - template, X - disabled, D - dynamic, I - invalid, A - active, * - default
0 T * group=default src-address=::/0 dst-address=::/0 protocol=all proposal=default template=yes
1 T group=ike2-gre src-address=192.168.99.2/32 dst-address=192.168.99.1/32 protocol=all proposal=ike2-gre template=yes
2 DA src-address=192.168.99.2/32 src-port=any dst-address=192.168.99.1/32 dst-port=any protocol=all action=encrypt level=unique ipsec-protocols=esp
tunnel=yes sa-src-address=172.17.2.1 sa-dst-address=172.17.2.2 proposal=ike2-gre ph2-count=1 |
A secure tunnel is now established between both sites which will encrypt all traffic between 192.168.99.2 <=> 192.168.99.1 addresses. We can use these addresses to create a GRE tunnel.
| Code Block |
|---|
|
/interface gre
add local-address=192.168.99.2 name=gre-tunnel1 remote-address=192.168.99.1 |
IKEv2 EAP between NordVPN and RouterOS
Example available here
Troubleshooting/FAQ
Phase 1 Failed to get a valid proposal
| Code Block |
|---|
|
[admin@MikroTik] /log> print
(..)
17:12:32 ipsec,error no suitable proposal found.
17:12:32 ipsec,error 10.5.107.112 failed to get valid proposal.
17:12:32 ipsec,error 10.5.107.112 failed to pre-process ph1 packet (side: 1, status 1).
17:12:32 ipsec,error 10.5.107.112 phase1 negotiation failed.
(..) |
Peers are unable to negotiate encryption parameters causing the connection to drop. To solve this issue, enable IPSec to debug logs and find out which parameters are proposed by the remote peer, and adjust the configuration accordingly.
| Code Block |
|---|
|
[admin@MikroTik] /system logging> add topics=ipsec,!debug |
| Code Block |
|---|
|
[admin@MikroTik] /log> print
(..)
17:21:08 ipsec rejected hashtype: DB(prop#1:trns#1):Peer(prop#1:trns#1) = MD5:SHA
17:21:08 ipsec rejected enctype: DB(prop#1:trns#2):Peer(prop#1:trns#1) = 3DES-CBC:AES-CBC
17:21:08 ipsec rejected hashtype: DB(prop#1:trns#2):Peer(prop#1:trns#1) = MD5:SHA
17:21:08 ipsec rejected enctype: DB(prop#1:trns#1):Peer(prop#1:trns#2) = AES-CBC:3DES-CBC
17:21:08 ipsec rejected hashtype: DB(prop#1:trns#1):Peer(prop#1:trns#2) = MD5:SHA
17:21:08 ipsec rejected hashtype: DB(prop#1:trns#2):Peer(prop#1:trns#2) = MD5:SHA
17:21:08 ipsec,error no suitable proposal found.
17:21:08 ipsec,error 10.5.107.112 failed to get valid proposal.
17:21:08 ipsec,error 10.5.107.112 failed to pre-process ph1 packet (side: 1, status 1).
17:21:08 ipsec,error 10.5.107.112 phase1 negotiation failed.
(..) |
In this example, the remote end requires SHA1 to be used as a hash algorithm, but MD5 is configured on the local router. Setting before the column symbol (:) is configured on the local side, parameter after the column symbol (:) is configured on the remote side.
"phase1 negotiation failed due to time up" what does it mean?
There are communication problems between the peers. Possible causes include - misconfigured Phase 1 IP addresses; firewall blocking UDP ports 500 and 4500; NAT between peers not properly translating IPsec negotiation packets. This error message can also appear when a local-address parameter is not used properly. More information available here.
Random packet drops or connections over the tunnel are very slow, enabling packet sniffer/torch fixes the problem?
Problem is that before encapsulation packets are sent to Fasttrack/FastPath, thus bypassing IPsec policy checking. The solution is to exclude traffic that needs to be encapsulated/decapsulated from Fasttrack, see configuration example here.
How to enable ike2?
For basic configuration enabling ike2 is very simple, just change exchange-mode in peer settings to ike2.
fatal NO-PROPOSAL-CHOSEN notify message?
Remote peer sent notify that it cannot accept proposed algorithms, to find the exact cause of the problem, look at remote peers debug logs or configuration and verify that both client and server have the same set of algorithms.
I can ping only in one direction?
A typical problem in such cases is strict firewall, firewall rules allow the creation of new connections only in one direction. The solution is to recheck firewall rules, or explicitly accept all traffic that should be encapsulated/decapsulated.
Can I allow only encrypted traffic?
Yes, you can, see "Allow only IPsec encapsulated traffic" examples.
I enable IKEv2 REAUTH on StrongSwan and got the error 'initiator did not reauthenticate as requested'
RouterOS does not support rfc4478, reauth must be disabled on StrongSwan.
