...
| Features | Description |
|---|---|
| Forwarding |
|
| Spanning Tree Protocol |
|
| Multicast Forwarding |
|
| Mirroring |
|
| VLAN |
|
| Quality of Service (QoS) |
|
| Access Control List |
|
...
| Info |
|---|
MikroTik Neighbor Discovery can be used to discover the IP address of the Mikrotik switch. LLDP is not supported. |
...
- Append - add a new item to the end of the list
- Apply All - applies current configuration changes
- Cut - removes an item from the list
- Clear - reset properties of the item
- Discard Changes - removes unsaved configuration
- Insert - add a new item to the list (places it before current item)
- Sort - sort VLAN table by VLAN-IDs; sort host table by MAC addresses
- Change Password - changes the password of the switch
- Logout - logout from the current switch
- Reboot - reboot the switch
- Reset Configuration - reset configuration back to factory defaults
- Choose File - browse for upgrade or backup file
- Upgrade - upgrade the firmware of the switch using the selected file
- Download & Upgrade - automatically try to download and upgrade the firmware, the PC which is running a web browser should be able to access the Internet
- Restore Backup - restore switch using a selected backup file
- Save Backup - generate and download backup file from the switch
...
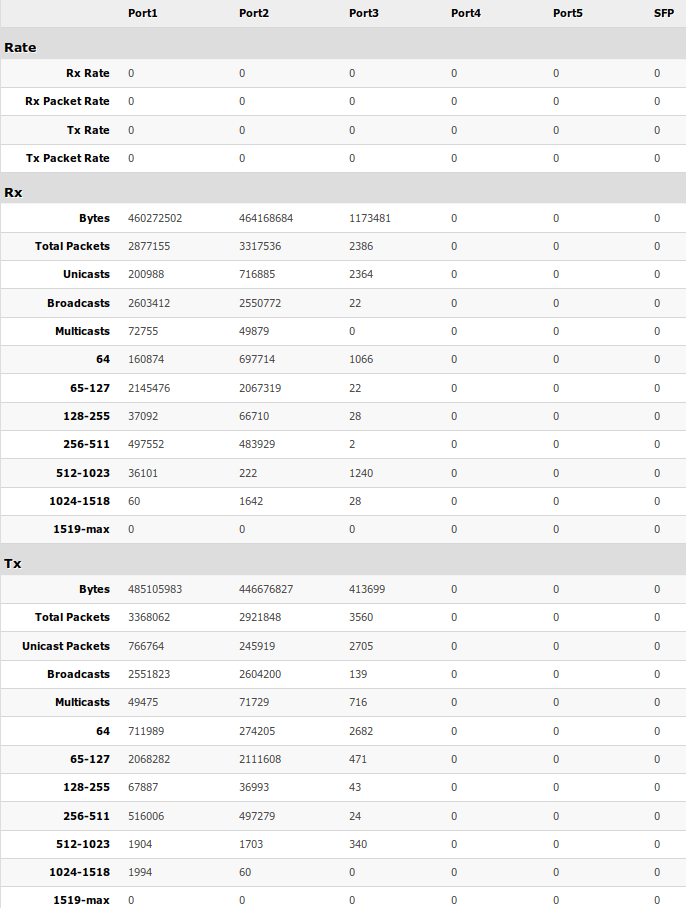
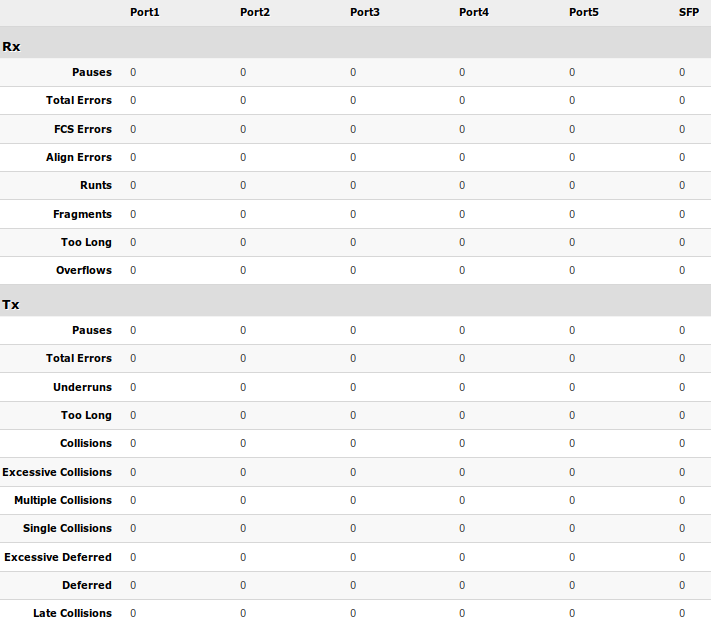
Provides detailed information about received and transmitted packets.
VLAN and VLANs
...
VLAN configuration for switch ports.
...
| Info |
|---|
VLAN modes |
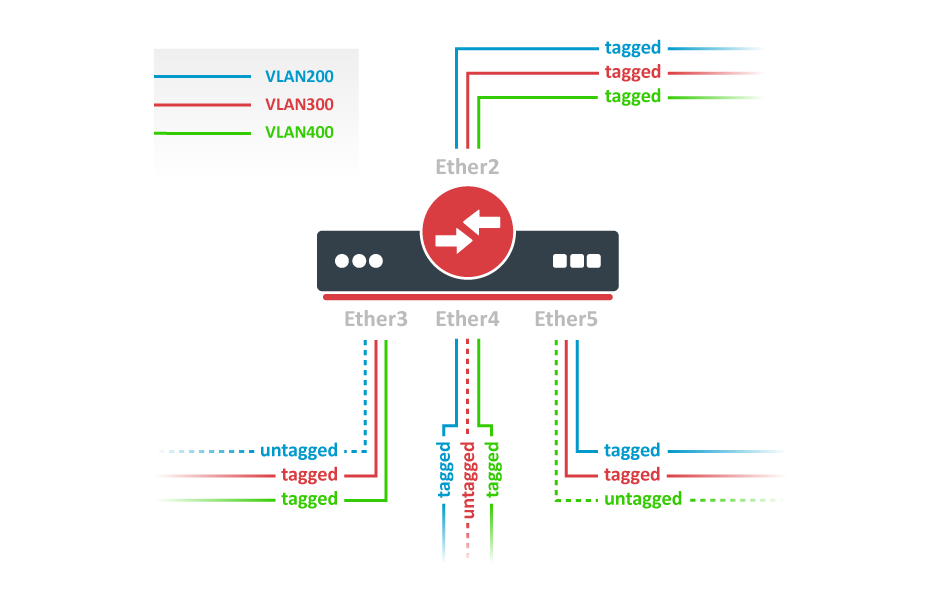
VLAN Configuration Examples
Trunk and Access Ports
Trunk and Hybrid Ports
Management access
...
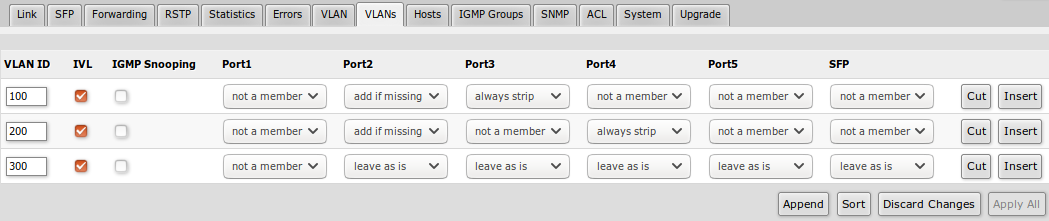
VLAN table specifies certain forwarding rules for packets that have a specific an IEEE 802.1Q tag. Basically, the table contains entries that map specific VLAN tag IDs to a group of one or more ports. Packets with VLAN tags leave switch through one or more ports that are set in the corresponding table entry. VLAN table works together with destination MAC lookup to determine egress ports. VLAN table supports up to 250 entries.
| Property | Description |
|---|---|
| VLAN ID | VLAN ID of the packet |
| IVL | Enables or disables independent VLAN learning (IVL) |
| IGMP Snooping | Enables or disables IGMP Snooping on the defined VLAN. When enabled, the switch will listen to IGMP Join and Leave requests from the defined VLAN and only forward traffic to ports, which have sent IGMP membership requests from the defined VLAN. When disabled, the switch will flood all VLAN member ports with Multicast traffic. |
| Ports | Each port has individual VLAN header options for each VLAN ID. Depending on VLAN mode if lookup is done in this table, the egress action of packets is processed by this option. The egress option from the VLAN tab is ignored. |
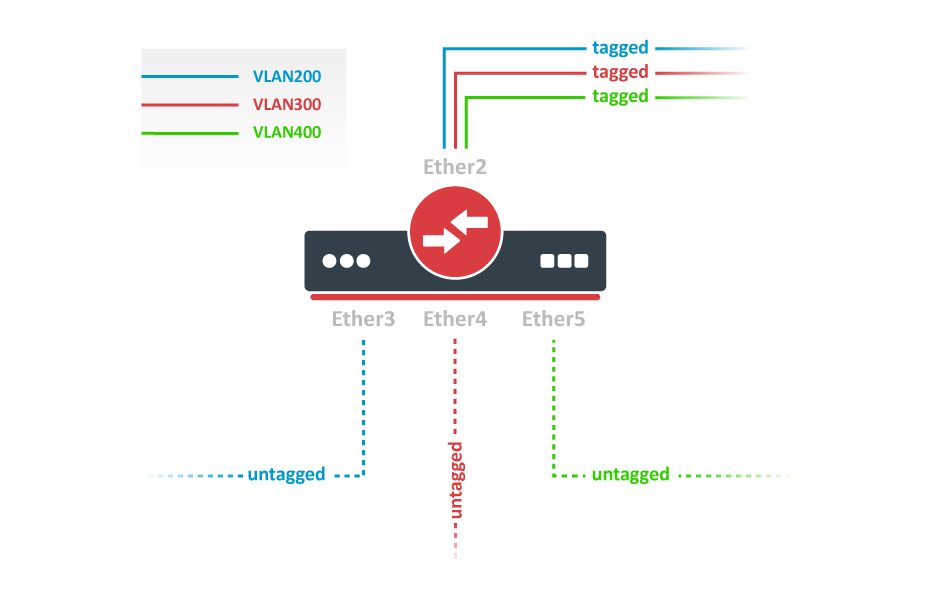
VLAN Configuration Examples
Trunk and Access Ports
Trunk and Hybrid Ports
Management access
Hosts
...
This table represents dynamically learned MAC address to port mapping entries. It can contain two kinds of entries: dynamic and static. Dynamic entries get added automatically, this is also called a learning process: when a switch receives a packet from a certain port, it adds the packet's source MAC address X and port it received the packet from to host table, so when a packet comes in with destination MAC address X it knows to which port it should forward the packet. If the destination MAC address is not present in the host table then it forwards the packet to all ports in the group (flood). Dynamic entries take about 5 minutes to time out.
...