...
| Phase 2 | ||
|---|---|---|
| Hash Algorithm | Encryption Algorithm | PFS Group |
| SHA1 | AES-256-CBC | none |
| SHA1 | AES-128-CBC | none |
| SHA1 | 3DES | none |
| SHA1 | DES | none |
| SHA1 | none | none |
macOS client configuration
Open the PKCS12 format certificate file on the macOS computer and install the certificate in the "System" keychain. It is necessary to mark the CA certificate as trusted manually since it is self-signed. Locate the certificate macOS Keychain Access app under the System tab and mark it as Always Trust.
...
| Phase 2 | ||
|---|---|---|
| Hash Algorithm | Encryption Algorithm | PFS Group |
| SHA256 | AES-256-CBC | none |
| SHA1 | AES-128-CBC | none |
| SHA1 | 3DES | none |
iOS client configuration
Typically PKCS12 bundle contains also a CA certificate, but iOS does not install this CA, so a self-signed CA certificate must be installed separately using PEM format. Open these files on the iOS device and install both certificates by following the instructions. It is necessary to mark the self-signed CA certificate as trusted on the iOS device. This can be done in Settings -> General -> About -> Certificate Trust Settings menu. When it is done, check whether both certificates are marked as "verified" under the Settings -> General -> Profiles menu.
...
| Phase 2 | ||
|---|---|---|
| Hash Algorithm | Encryption Algorithm | PFS Group |
| SHA256 | AES-256-CBC | none |
| SHA1 | AES-128-CBC | none |
| SHA1 | 3DES | none |
| Note |
|---|
If you are connected to the VPN over WiFi, the iOS device can go into sleep mode and disconnect from the network. |
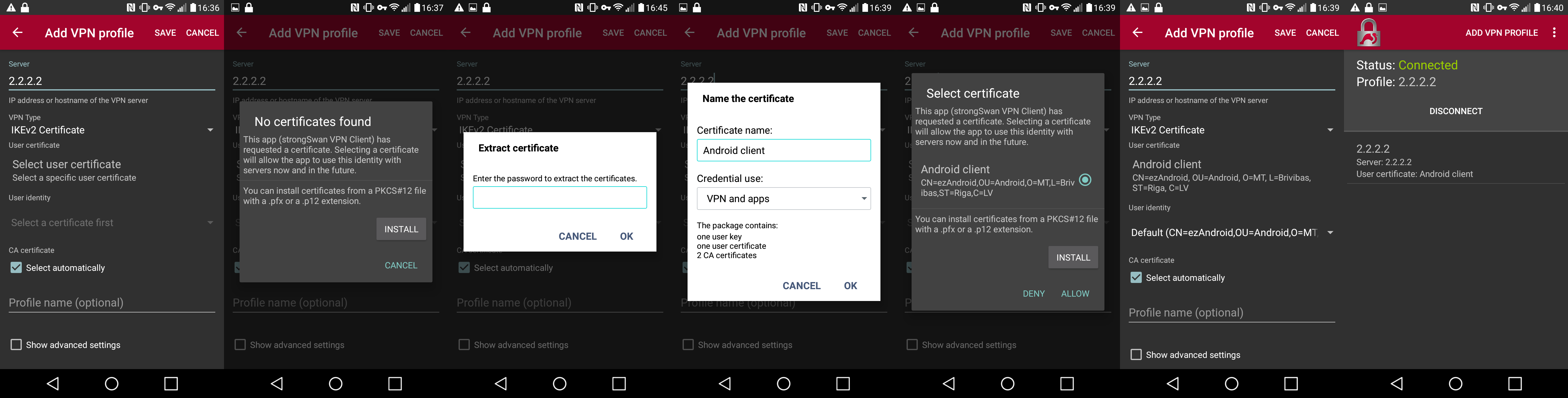
Android (strongSwan) client configuration
Currently, there is no IKEv2 native support in Android, however, it is possible to use strongSwan from Google Play Store which brings IKEv2 to Android. StrongSwan accepts PKCS12 format certificates, so before setting up the VPN connection in strongSwan, make sure you download the PKCS12 bundle to your Android device. When it is done, create a new VPN profile in strongSwan, type in the server IP, and choose "IKEv2 Certificate" as VPN Type. When selecting a User certificate, press Install and follow the certificate extract procedure by specifying the PKCS12 bundle. Save the profile and test the connection by pressing on the VPN profile.
It is possible to specify custom encryption settings in strongSwan by ticking the "Show advanced settings" checkbox. Currently, strongSwan by default is compatible with the following Phase 1 ( profiles) and Phase 2 ( proposals) proposal sets:
| Phase 1 | ||
|---|---|---|
| Hash Algorithm | Encryption Algorithm | DH Group |
| SHA* | AES-*-CBC | modp2048 |
| SHA* | AES-*-CBC | ecp256 |
| SHA* | AES-*-CBC | ecp384 |
| SHA* | AES-*-CBC | ecp521 |
| SHA* | AES-*-CBC | modp3072 |
| SHA* | AES-*-CBC | modp4096 |
| SHA* | AES-*-CBC | modp6144 |
| SHA* | AES-*-CBC | modp8192 |
| SHA* | AES-*-GCM | modp2048 |
| SHA* | AES-*-GCM | ecp256 |
| SHA* | AES-*-GCM | ecp384 |
| SHA* | AES-*-GCM | ecp521 |
| SHA* | AES-*-GCM | modp3072 |
| SHA* | AES-*-GCM | modp4096 |
| SHA* | AES-*-GCM | modp6144 |
| SHA* | AES-*-GCM | modp8192 |
| Phase 2 | ||
|---|---|---|
| Hash Algorithm | Encryption Algorithm | PFS Group |
| none | AES-256-GCM | none |
| none | AES-128-GCM | none |
| SHA256 | AES-256-CBC | none |
| SHA512 | AES-256-CBC | none |
| SHA1 | AES-256-CBC | none |
| SHA256 | AES-192-CBC | none |
| SHA512 | AES-192-CBC | none |
| SHA1 | AES-192-CBC | none |
| SHA256 | AES-128-CBC | none |
| SHA512 | AES-128-CBC | none |
| SHA1 | AES-128-CBC | none |
Linux (strongSwan) client configuration
Download the PKCS12 certificate bundle and move it to /etc/ipsec.d/private directory.
Add exported passphrase for the private key to /etc/ipsec.secrets file where "strongSwan_client.p12" is the file name and "1234567890" is the passphrase.
| Code Block | ||
|---|---|---|
| ||
: P12 strongSwan_client.p12 "1234567890" |
Add a new connection to /etc/ipsec.conf file
| Code Block | ||
|---|---|---|
| ||
conn "ikev2"
keyexchange=ikev2
ike=aes128-sha1-modp2048
esp=aes128-sha1
leftsourceip=%modeconfig
leftcert=strongSwan_client.p12
leftfirewall=yes
right=2.2.2.2
rightid="CN=2.2.2.2"
rightsubnet=0.0.0.0/0
auto=add |
You can now restart (or start) the ipsec daemon and initialize the connection
| Code Block | ||
|---|---|---|
| ||
$ ipsec restart
$ ipsec up ikev2 |