| Table of Contents |
|---|
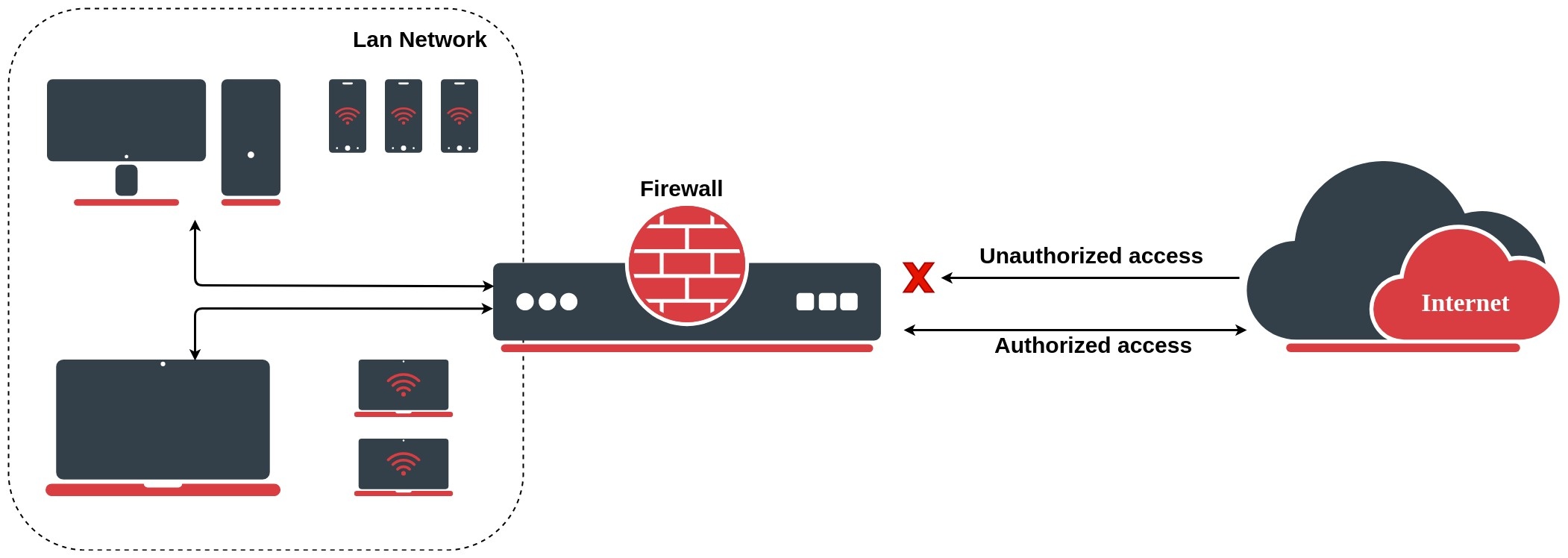
The firewall implements stateful (by utilizing connection tracking) and stateless packet filtering and thereby provides security functions that are used to manage data flow to, from, and through the router. Along with the Network Address Translation (NAT), it serves as a tool for preventing unauthorized access to directly attached networks and the router itself as well as a filter for outgoing traffic.
...
To completely understand firewall rules, first, you have to understand various states which might apply to a particular network packet. There are five connection states in RouterOS:
- NEW - The The NEW state tells us that the packet is the first packet that we see. This means that the first packet that the conntrack module sees, within a specific connection, will be matched. For example, if we see an a SYN packet and it is the first packet in a connection that we see, it will match;
- ESTABLISHED - The ESTABLISHED state has seen traffic in both directions and will then continuously match those packets. ESTABLISHED connections are fairly easy to understand. The only requirement to get into an ESTABLISHED state is that one host sends a packet and that it, later on, gets a reply from the other host. The NEW state will upon receipt of the reply packet to or through the firewall change to the ESTABLISHED state;
- RELATED - A connection is considered RELATED when it is related to another already ESTABLISHED connection. For a connection to be considered as RELATED, we must first have a connection that is considered ESTABLISHED. The ESTABLISHED connection will then spawn a connection outside of the main connection. The newly spawned connection will then be considered RELATED, for example, a packet that begins the FTP data connection;
- INVALID - The INVALID state means that the packet can't be identified or that it does not have any state. It is suggested to DROP everything in this state;
- UNTRACKED - A packet that was set to bypass connection tracking in the Firewall RAW table;
...
Let's look at the basic firewall setup to protect the router. By default RouterOS firewall accepts everything, blocking is achieved by adding a filter rule to drop everything at the end of all rules. For out our router we want to allow only ICMP, ssh, and Winbox and drop the rest:
| Code Block | ||
|---|---|---|
| ||
/ip firewall filter add chain=input connection-state=invalid action=drop comment="Drop Invalid connections" add chain=input connection-state=established,related,untracked action=accept comment="Allow Established/Related/Untracked connections" add chain=input protocol=icmp action=accept comment="Allow ICMP" add chain=input protocol=tcp ports=8291,22 action=accept comment="Allow Winbox and SSH" add chain=input action=drop comment="Drop everything else" |
RouterOS also allows to filter filtering packets before connection tracking and selectively send sends only specific traffic to connection tracking. This allows us to significantly reduce the load on the CPU and mitigate DOS/DDoS attacks. Configuration of such rules is done in the RAW filtering table.
Additional /ip firewall filter configuration examples find are found under the Building Your First Firewall section.
...
A list of tracked connections can be seen in the /ip firewall connection for ipv4 and /ipv6 firewall connection for IPv6.
...
If a packet is not new it can belong to either an established or related connection or not belong to any connection making it invalid. A packet with an established state, as most of you already guessed, belongs to an existing connection from the connection tracking table. A related state is very similar, except that the packet belongs to a connection that is related to one of the existing connections, for example, ICMP error packets or FTP data connection packets.
...
| Note |
|---|
Such a rule set must not be applied on routers with asymmetric routing, because asymmetrically routed packets may be considered invalid and dropped. |
FastTrack
IPv4 FastTrack handler is automatically used for marked connections. Use firewall action "fasttrack-connection" to mark connections for FastTrack. Currently, only TCP and UDP connections can be actually FastTracked (even though any connection can be marked for FastTrack). IPv4 FastTrack handler supports NAT (SNAT, DNAT, or both).
Note that not all packets in a connection can be FastTracked, so it is likely to see some packets going through a slow path even though the connection is marked for FastTrack. This is the reason why fasttrack-connection is usually followed by an identical "action=accept" rule. FastTrack packets bypass firewall, connection tracking, simple queues, queue tree with parent=global, IP accounting, IPSec, hotspot universal client, and VRF assignment, so it is up to the administrator to make sure FastTrack does not interfere with other configuration.
Requirements
IPv4 FastTrack is active if the following conditions are met:
- no mesh, metarouter interface configuration;
- sniffer, torch, or traffic generator is not running;
- /tool mac-scan is not actively used;
- /tool ip-scan is not actively used;
- FastPath and Route cache is enabled under IP/Settings
Example
For example, for SOHO routers with factory default configuration, you could FastTrack all LAN traffic with this one rule placed at the top of the Firewall Filter. The same configuration accept rule is required:
| Code Block | ||
|---|---|---|
| ||
/ip firewall filter add chain=forward action=fasttrack-connection connection-state=established,related
/ip firewall filter add chain=forward action=accept connection-state=established,related |
| Tip |
|---|
|
| Note |
|---|
Queues (except Queue Trees parented to interfaces), firewall filter, and mangle rules will not be applied for FastTracked traffic. |
Services
This section lists protocols and ports used by various MikroTik RouterOS services. It helps you to determine why your MikroTik router listens to certain ports, and what you need to block/allow in case you want to prevent or grant access to certain services.
The default services are:
| Property | Description |
|---|---|
| telnet | Telnet service |
| ftp | FTP service |
| www | Webfig |
| HTTP service | |
| ssh | SSH service |
| www-ssl | Webfig HTTPS service |
| api | API service |
| winbox | Responsible for Winbox tool access, as well as Tik-App smartphone app and Dude probe |
| api-ssl | API over SSL service |
Properties
Note that it is not possible to add new services, only existing service modifications are allowed.
| Property | Description |
|---|---|
| address (IP address/netmask | IPv6/0..128; Default: ) | List of IP/IPv6 prefixes from which the service is accessible. |
| certificate (name; default: none) | The name of the certificate used by a particular service. Applicable only for services that depend on certificates (www-ssl, api-ssl) |
| name (name; default: none) | Service name |
| port (integer: 1..65535; Default: ) | The port particular service listens on |
To restrict Winbox service access to the device only from the 192.168.88.0/24 subnet, we have to configure the following:
...
Firewall address lists allow a user to create lists of IP addresses grouped together under a common name. Firewall filter, Mangle, and NAT facilities can then use those address lists to match packets against them. The address list records can also be updated dynamically via the action=add-src-to-address-listlist or action=add-dst-to-address-list items found in NAT, Mangle, and Filter facilities.
Firewall rules with action add-src-to-address-list or add-dst-to-address-list works work in passthrough mode, which means that the matched packets will be passed to the next firewall rules. A basic example of a dynamically created address-list:
...
| Code Block | ||
|---|---|---|
| ||
/ip firewall layer7-protocol add name=rdp regexp="rdpdr.*cliprdr.*rdpsnd" |
| Tip |
|---|
If the Layer7 matcher recognizes the connection, then the rule marks this connection as its "own" and other rules do not look at this connection anymore even if the two firewall rules with Layer7 matcher are identical. |
| Warningnote |
|---|
When a user uses HTTPS, Layer7 rules will not be able to match this traffic. Only unencrypted HTTP can be matched. |
...