...
- certificate is not yet valid - notBefore certificate date is after the current time;
- certificate has expired - certificate expiry date is before the current time;
- cinvalid certificate purpose - the supplied certificate cannot be used for the specified purpose;
- cself signed certificate in a chain - the certificate chain could be built up using the untrusted certificates but the root could not be found locally;
- cunable to get issuer certificate locally - CA certificate is not imported locally;
- cserver's IP address does not match certificate - server address verification is enabled, but the address provided in certificate does not match the server's address;
Configuration example
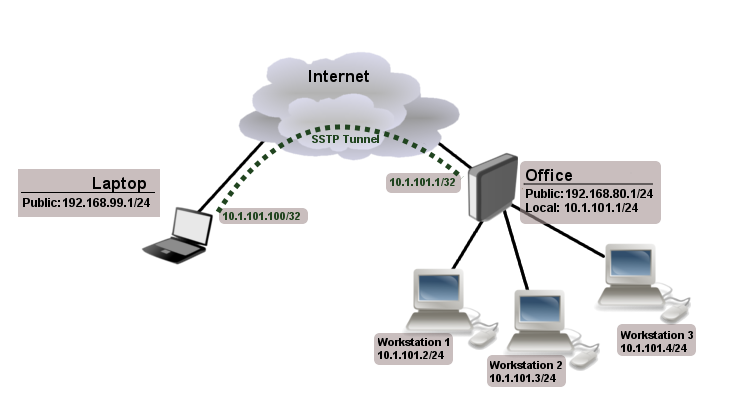
The following example shows how to connect a computer to a remote office network over secure SSTP encrypted tunnel giving that computer an IP address from the same network as the remote office has (without the need for bridging over EoIP tunnels)
Consider the following setup:
Office router is connected to the internet through ether1. Workstations are connected to ether2. A laptop is connected to the internet and can reach Office router's public IP (in our example it is 192.168.80.1).
| Note |
|---|
Before you begin to configure SSTP you need to create a server certificate and import it into the router. |
Now it is time to create a user:
...
Quick Example
SSTP Client
In the following configuration example, e will create a simple SSTP client without using a certificate:
| Code Block | ||
|---|---|---|
| ||
[admin@MikroTik > interface sstp-client add connect-to=192.168.62.2 disabled=no name=sstp-out1 password=StrongPass profile=default-encryption user=MT-User [admin@MikroTik > interface sstp-client print Flags: X - disabled; R - running 0 R name=" |
...
sstp-out1" max-mtu=1500 max-mru=1500 mrru=disabled connect-to=192.168.62.2:443 http-proxy=0.0.0.0:443 certificate=none verify-server-certificate=no verify-server-address-from-certificate=yes user="MT-User" password=" |
...
StrongPass"
profile=default-encryption keepalive-timeout=60 add-default-route=no dial-on-demand=no
authentication=pap,chap,mschap1,mschap2 pfs=no tls-version=any |
SSTP Server
We will configure PPP secret for a particular user, afterwards simply enable an SSTP server:
| Code Block | ||
|---|---|---|
| ||
[admin@MikroTik] > ppp secret add local-address=10. |
...
0. |
...
0.1 |
...
Notice that SSTP local address is the same as the router's address on the local interface and the remote address is from the same range as the local network (10.1.101.0/24).
Next step is to enable SSTP server and SSTP client on the laptop:
...
name=MT-User password=StrongPass remote-address=10.0.0.5 service=sstp [admin@MikroTik] > interface sstp-server server set default-profile=default-encryption enabled=yes |
...
[admin@MikroTik] > interface sstp-server server print |
...
|
...
|
...
|
...
|
...
|
...
|
...
|
...
|
...
|
...
|
...
|
...
|
...
|
...
|
...
|
...
|
...
|
...
|
...
enabled: |
...
Notice that authentication is set to MS-CHAP. These are the only authentication options that are valid to establish a secure tunnel.
SSTP client from the laptop should connect to routers public IP which in our example is 192.168.80.1.
Please, consult the respective manual on how to set up an SSTP client with the software you are using. If you set up SSTP clients on Windows and self-signed certificates are used, then a CA certificate should be added to a trusted root.
To verify if SSTP client is connected
yes |
...
|
...
|
...
|
...
|
...
|
...
|
...
|
...
|
...
|
...
|
...
|
...
port: |
...
443 |
...
|
...
|
...
max-mtu: 1500 |
...
...
|
...
max-mru: |
...
1500 |
...
|
...
|
...
|
...
|
...
|
...
mrru: disabled |
...
|
...
keepalive-timeout: 60 |
...
default-profile: |
...
default-encryption |
...
authentication: |
...
pap,chap,mschap1,mschap2 |
...
certificate: none verify-client-certificate: no |
...
|
...
|
...
|
...
pfs: no |
...
|
...
At this point (when SSTP client is successfully connected) if you try to ping any workstation from a laptop, ping will time out, because the Laptop is unable to get ARP`s from workstations. The solution is to set up proxy-arp on a local interface
...
|
...
|
...
|
...
|
...
tls-version: any |