...
Network Address Translation is an Internet standard that allows hosts on local area networks to use one set of IP addresses for internal communications and another set of IP addresses for external communications. A LAN that uses NAT is ascribed as a natted network. For NAT to function, there should be a NAT gateway in each natted network. The NAT gateway (NAT router) performs IP address rewriting on the way packet while packets travel from/to LAN.
Nat matches only the first packet of the connection, connection tracking remembers the action and performs on all other packets belonging to the same connection.
| Warning |
|---|
Whenever NAT rules are changed or added, the connection tracking table should be cleared otherwise NAT rules may seem to be not functioning correctly until the connection entry expires. |
...
- source NAT or srcnat. This type of NAT is performed on packets that are originated from a natted network. A NAT router replaces the private source address of an IP packet with a new public IP address as it travels through the router. A reverse operation is applied to the reply packets traveling in the other direction.
- destination NAT or dstnat. This type of NAT is performed on packets that are destined for the natted network. It is most commonly used to make hosts on a private network to be accessible from the Internet. A NAT router performing dstnat replaces the destination IP address of an IP packet as it travels through the router towards toward a private network.
Since RouterOS v7 the firewall NAT has two new INPUT and OUTPUT chains which are traversed for packets delivered to and sent from applications running on the local machine:
...
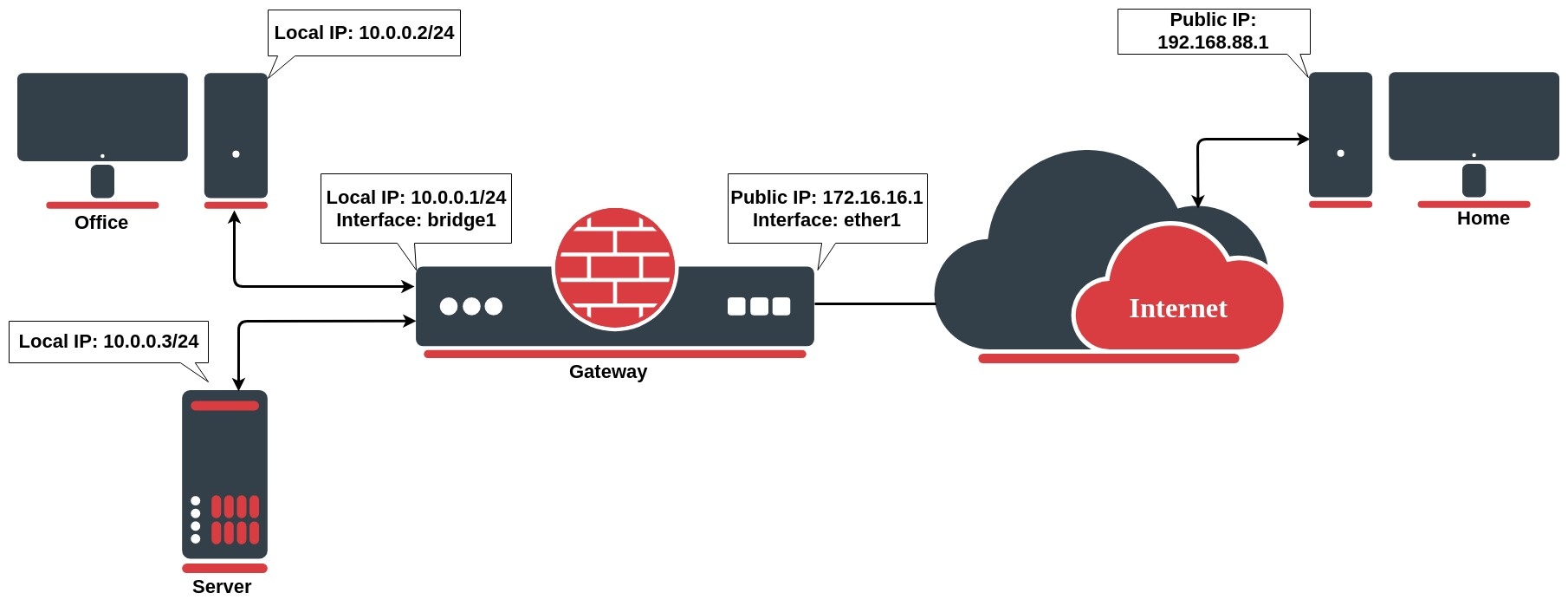
Network address translation works by modifying network address information in the packets packet's IP header. Let`s take a look at the common setup where a network administrator wants to access an office server from the internet.
...
If you want to hide your local devices behind your public IP address received from the ISP, you should you should configure the source network address translation (masquerading) feature of the MikroTik router.
Let`s assume you want to hide both the office computer and server behind the public IP 172.16.16.1, the rule will look like the following one:
...
Now your ISP will see all the requests coming with IP 172.16.16.1 and they will not see your LAN network IP addresses.
Masquerade
Firewall NAT action=masqueradeis a unique subversion of action=srcnat, it was designed for specific use in situations when public IP can randomly change, for example, DHCP server change changes assigned IP or PPPoE tunnel after disconnect gets a different IP, in short - when public IP is dynamic.
...
Every time when interface disconnects and/or its IP address changes, the router will clear all masqueraded connection tracking entries related to the interface, this way improving system recovery time after public IP change. If srcnat is used instead of masquerade, connection tracking entries remain and connections can simply resume after a link failure.
...
To overcome these limitations RouterOS includes a number of so-called NAT helpers, that enable NAT traversal for various protocols. When action=srcnat is used instead, connection tracking entries remain and connections can simply resume.
...
Because of the nature of such a setup, it is also called NAT444, as opposed to a NAT44 network for a 'normal' NAT environment, three different IPv4 address spaces are involved.
...
- 2.2.2.2 - public IP address,
- public_if - interface on providers provider's edge router connected to the internet
...
Service providers may be required to log of MAPed addresses, in a large CGN deployed network that which may be a problem. Fortunately, RFC 7422 suggests a way to manage CGN translations in such a way as to significantly reduce the amount of logging required while providing traceability for abuse response.
...
The six local values can be adjusted and the script can be either simply pasted in the terminal or it can be stored in the system script section, in case the configuration needs to be regenerated later.
After execution, you should get a set of rules:
...
Hairpin network address translation (NAT Loopback) is where the device on the LAN is able to LAN can access another machine on the LAN via the public IP address of the gateway router.
In the above example, the gateway router has the following following dst-nat configuration rule:
| Code Block | ||
|---|---|---|
| ||
/ip firewall nat add chain=dstnat action=dst-nat dst-address=172.16.16.1 dst-port=443 to-addresses=10.0.0.3 to-ports=443 protocol=tcp |
When a user from the PC at home establishes a connection to the webserverweb server, the router performs DST NAT as configured:
- the client sends a packet with a source IP address of 192.168.88.1 to a destination IP address of 172.16.16.1 on port 443 to request some web resources;
- the router destination NAT`s the packet to 10.0.0.3 and replaces the destination IP address in the packet accordingly. The source IP address stays the same: 192.168.88.1;
- the server replies to the client's request and the reply packet have has a source IP address of 10.0.0.3 and a destination IP address of 192.168.88.1.
- the router determines that the packet is part of a previous connection and undoes the destination NAT, and puts the original destination IP address into the source IP address field. The destination IP address is 192.168.88.1, and the source IP address is 172.16.16.1;
- The client receives the reply packet it expects, and the connection is established;
...
This mapping allows running source-independent filtering, which allows forwarding packets from any source from WAN to mapped internal IP and port. Following The following rule enables filtering:
| Code Block | ||
|---|---|---|
| ||
/ip firewall nat add action=endpoint-independent-nat chain=dstnat in-interface=WAN protocol=udp |
...
Additionally, endpoint-independent-nat can take a few other parameters:
randomize-port- randomize to which public port connections will be mapped.
...
| Property | Description |
|---|---|
| action (action name; Default: accept) | Action to take if a packet is matched by the rule:
|
| address-list (string; Default: ) | Name of the address list to be used. Applicable if action is add-dst-to-address-list or add-src-to-address-list |
| address-list-timeout (none-dynamic | none-static | time; Default: none-dynamic) | Time interval after which the address will be removed from the address list specified by address-list parameter. Used in conjunction with add-dst-to-address-list or add-src-to-address-list actions
|
| chain (name; Default: ) | Specifies to which chain rule will be added. If the input does not match the name of an already defined chain, a new chain will be created |
| comment (string; Default: ) | Descriptive comment for the rule |
| connection-bytes (integer-integer; Default: ) | Matches packet only if a given amount of bytes has been transferred through the particular connection. 0 - means infinity, for example connection-bytes=2000000-0 means that the rule matches if more than 2MB has been transferred through the relevant connection |
| connection-limit (integer,netmask; Default: ) | Matches connections per address or address block after a given value is reached |
| connection-mark (no-mark | string; Default: ) | Matches packets marked via mangle facility with particular connection mark. If a no-mark is set, the rule will match any unmarked connection |
| connection-rate (Integer 0..4294967295; Default: ) | Connection Rate is a firewall matcher that allows capturing traffic based on the present speed of the connection |
| connection-type (ftp | h323 | irc | pptp | quake3 | sip | tftp; Default: ) | Matches packets from related connections based on information from their connection tracking helpers. A relevant connection helper must be enabled under /ip firewall service-port |
| content (string; Default: ) | Match packets that contain specified text |
| dscp (integer: 0..63; Default: ) | Matches DSCP IP header field. |
| dst-address (IP/netmask | IP range; Default: ) | Matches packets whose destination is equal to a specified IP or falls into a specified IP range. |
| dst-address-list (name; Default: ) | Matches the destination address of a packet against a user-defined address list |
| dst-address-type (unicast | local | broadcast | multicast; Default: ) | Matches destination address type:
|
| dst-limit (integer[/time],integer,dst-address | dst-port | src-address[/time]; Default: ) | Matches packets until a given PPS limit is exceeded. As opposed to the limit matcher, every destination IP address/destination port has its own limit. Parameters are written in the following format: count[/time],burst,mode[/expire].
|
| dst-port (integer[-integer]: 0..65535; Default: ) | List of destination port numbers or port number ranges in format Range[,Port], for example, dst-port=123-345,456-678 |
| fragment (yes|no; Default: ) | Matches fragmented packets. The first (starting) fragment does not count. If connection tracking is enabled there will be no fragments as the system automatically assembles every packet |
| hotspot (auth | from-client | http | local-dst | to-client; Default: ) | Matches packets received from HotSpot clients against various HotSpot matchers.
|
| icmp-options (integer:integer; Default: ) | Matches ICMP type: code fields |
| in-bridge-port (name; Default: ) | Actual interface the packet has entered the router if the incoming interface is a bridge |
| in-interface (name; Default: ) | Interface the packet has entered the router |
| ingress-priority (integer: 0..63; Default: ) | Matches ingress the priority of the packet. Priority may be derived from VLAN, WMM or MPLS EXP bit. |
| ipsec-policy (in | out, ipsec | none; Default: ) | Matches the policy used by IPSec. Value is written in the following format: direction, policy. The direction is Used to select whether to match the policy used for decapsulation or the policy that will be used for encapsulation.
For example, if a router receives an IPsec encapsulated Gre packet, then the rule |
| ipv4-options (any | loose-source-routing | no-record-route | no-router-alert | no-source-routing | no-timestamp | none | record-route | router-alert | strict-source-routing | timestamp; Default: ) | Matches IPv4 header options.
|
| jump-target (name; Default: ) | Name of the target chain to jump to. Applicable only if action=jump |
| layer7-protocol (name; Default: ) | Layer7 filter name defined in layer7 protocol menu. |
| limit (integer,time,integer; Default: ) | Matches packets until a given PPS limit is exceeded. Parameters are written in the following format: count[/time],burst.
|
| log (yes | no; Default: no) | Add a message to the system log containing the following data: in-interface, out-interface, src-mac, protocol, src-ip:port->dst-ip:port, and length of the packet. |
| log-prefix (string; Default: ) | Adds specified text at the beginning of every log message. Applicable if action=log or log=yes configured. |
| out-bridge-port (name; Default: ) | Actual interface the packet is leaving the router if the outgoing interface is a bridge |
| out-interface (; Default: ) | Interface the packet is leaving the router |
| packet-mark (no-mark | string; Default: ) | Matches packets marked via mangle facility with particular packet mark. If no-mark is set, the rule will match any unmarked packet |
| packet-size (integer[-integer]:0..65535; Default: ) | Matches packets of specified size or size range in bytes |
| per-connection-classifier (ValuesToHash:Denominator/Remainder; Default: ) | PCC matcher allows dividing traffic into equal streams with the ability to keep packets with a specific set of options in one particular stream |
| port (integer[-integer]: 0..65535; Default: ) | Matches if any (source or destination) port matches the specified list of ports or port ranges. Applicable only if protocol is TCP or UDP |
| protocol (name or protocol ID; Default: tcp) | Matches particular IP protocol specified by protocol name or number |
| psd (integer,time,integer,integer; Default: ) | Attempts to detect TCP and UDP scans. Parameters are in the following format WeightThreshold, DelayThreshold, LowPortWeight, HighPortWeight
|
| random (integer: 1..99; Default: ) | Matches packets randomly with a given probability |
| routing-mark (string; Default: ) | Matches packets marked by mangle facility with particular routing mark |
| same-not-by-dst (yes | no; Default: ) | Specifies whether to take into account or not the destination IP address when selecting a new source IP address. Applicable if action=same |
| src-address (Ip/Netmaks, Ip range; Default: ) | Matches packets whose source is equal to a specified IP or falls into a specified IP range. |
| src-address-list (name; Default: ) | Matches the source address of a packet against a user-defined address list |
| src-address-type (unicast | local | broadcast | multicast; Default: ) | Matches source address type:
|
| src-port (integer[-integer]: 0..65535; Default: ) | List of source ports and ranges of source ports. Applicable only if a protocol is TCP or UDP. |
| src-mac-address (MAC address; Default: ) | Matches the source MAC address of the packet |
| tcp-mss (integer[-integer]: 0..65535; Default: ) | Matches the TCP MSS value of an IP packet |
| time (time-time,sat | fri | thu | wed | tue | mon | sun; Default: ) | Allows to create a filter based on the packets' arrival time and date or, for locally generated packets, departure time and date |
| to-addresses (IP address[-IP address]; Default: 0.0.0.0) | Replace the original address with the specified one. Applicable if action is dst-nat, netmap, same, src-nat |
| to-ports (integer[-integer]: 0..65535; Default: ) | Replace the original port with the specified one. Applicable if action is dst-nat, redirect, masquerade, netmap, same, src-nat |
| ttl (integer: 0..255; Default: ) | Matches packets packet's TTL value |
Stats
| Property | Description |
|---|---|
| bytes (integer) | The total amount of bytes matched by the rule |
| packets (integer) | The total amount of packets matched by the rule |
...
| Property | Description |
|---|---|
| action (action name; Default: accept) | Action to take if a packet is matched by the rule:
|
| address-list (string; Default: ) | Name of the address list to be used. Applicable if action is add-dst-to-address-list or add-src-to-address-list |
| address-list-timeout (none-dynamic | none-static | time; Default: none-dynamic) | Time interval after which the address will be removed from the address list specified by address-list parameter. Used in conjunction with add-dst-to-address-list or add-src-to-address-list actions
|
| chain (name; Default: ) | Specifies to which chain rule will be added. If the input does not match the name of an already defined chain, a new chain will be created |
| comment (string; Default: ) | Descriptive comment for the rule |
| connection-bytes (integer-integer; Default: ) | Matches packets only if a given amount of bytes has been transferred through the particular connection. 0 - means infinity, for example connection-bytes=2000000-0 means that the rule matches if more than 2MB has been transferred through the relevant connection |
| connection-limit (integer,netmask; Default: ) | Matches connections per address or address block after a given value is reached |
| connection-mark (no-mark | string; Default: ) | Matches packets marked via mangle facility with particular connection mark. If no-mark is set, the rule will match any unmarked connection |
| connection-rate (Integer 0..4294967295; Default: ) | Connection Rate is a firewall matcher that allows capturing traffic based on the present speed of the connection |
| connection-state (established | invalid | new | related | untracked; Default: ) | Interprets the connection tracking analytics data for a particular packet:
|
| connection-type (ftp | h323 | irc | pptp | quake3 | sip | tftp; Default: ) | Matches packets from related connections based on information from their connection tracking helpers. A relevant connection helper must be enabled under /ip firewall service-port |
| content (string; Default: ) | Match packets that contain specified text |
| dscp (integer: 0..63; Default: ) | Matches DSCP IP header field. |
| dst-address (IP/netmask | IP range; Default: ) | Matches packets whose destination is equal to a specified IP or falls into a specified IP range. |
| dst-address-list (name; Default: ) | Matches the destination address of a packet against a user-defined address list |
| dst-address-type (unicast | local | broadcast | multicast; Default: ) | Matches destination address type:
|
| dst-limit (integer[/time],integer,dst-address | dst-port | src-address[/time]; Default: ) | Matches packets until a given PPS limit is exceeded. As opposed to the limit matcher, every destination IP address/destination port has its own limit. Parameters are written in the following format: count[/time],burst,mode[/expire].
|
| dst-port (integer[-integer]: 0..65535; Default: ) | List of destination port numbers or port number ranges in format Range[,Port], for example, dst-port=123-345,456-678 |
| icmp-options (integer:integer; Default: ) | Matches ICMP type: code fields |
| in-bridge-port (name; Default: ) | Actual interface the packet has entered the router if the incoming interface is a bridge |
| in-bridge-port-list (name; Default: ) | Set of interfaces defined in interface list. Works the same as in-bridge-port |
| in-interface (name; Default: ) | Interface the packet has entered the router |
| in-interface-list (name; Default: ) | Set of interfaces defined in interface list. Works the same as in-interface |
| ingress-priority (integer: 0..63; Default: ) | Matches ingress the priority of the packet. Priority may be derived from VLAN, WMM or MPLS EXP bit. |
| ipsec-policy (in | out, ipsec | none; Default: ) | Matches the policy used by IPSec. Value is written in the following format: direction, policy. The direction is Used to select whether to match the policy used for decapsulation or the policy that will be used for encapsulation.
For example, if a router receives an IPsec encapsulated Gre packet, then the rule |
| jump-target (name; Default: ) | Name of the target chain to jump to. Applicable only if action=jump |
| layer7-protocol (name; Default: ) | Layer7 filter name defined in layer7 protocol menu. |
| limit (integer,time,integer; Default: ) | Matches packets until a given PPS limit is exceeded. Parameters are written in the following format: count[/time],burst.
|
| log (yes | no; Default: no) | Add a message to the system log containing the following data: in-interface, out-interface, src-mac, protocol, src-ip:port->dst-ip:port, and length of the packet. |
| log-prefix (string; Default: ) | Adds specified text at the beginning of every log message. Applicable if action=log or log=yes configured. |
| out-bridge-port (name; Default: ) | Actual interface the packet is leaving the router if the outgoing interface is a bridge |
| out-bridge-port-list (name; Default: ) | Set of interfaces defined in interface list. Works the same as out-bridge-port |
| out-interface (; Default: ) | Interface the packet is leaving the router |
| out-interface-list (name; Default: ) | Set of interfaces defined in interface list. Works the same as out-interface |
| packet-mark (no-mark | string; Default: ) | Matches packets marked via mangle facility with particular packet mark. If no-mark is set, the rule will match any unmarked packet |
| packet-size (integer[-integer]:0..65535; Default: ) | Matches packets of specified size or size range in bytes |
| per-connection-classifier (ValuesToHash:Denominator/Remainder; Default: ) | PCC matcher allows dividing traffic into equal streams with the ability to keep packets with a specific set of options in one particular stream |
| port (integer[-integer]: 0..65535; Default: ) | Matches if any (source or destination) port matches the specified list of ports or port ranges. Applicable only if protocol is TCP or UDP |
| protocol (name or protocol ID; Default: tcp) | Matches particular IP protocol specified by protocol name or number |
| priority (integer: 0..63; Default:) | Matches the packet's priority after a new priority has been set. Priority may be derived from VLAN, WMM, DSCP, MPLS EXP bit, or from the priority that has been set using the set-priority action. |
| random (integer: 1..99; Default: ) | Matches packets randomly with a given probability |
| routing-mark (string; Default: ) | Matches packets marked by mangle facility with particular routing mark |
| src-address (Ip/Netmaks, Ip range; Default: ) | Matches packets whose source is equal to a specified IP or falls into a specified IP range. |
| src-address-list (name; Default: ) | Matches the source address of a packet against a user-defined address list |
| src-address-type (unicast | local | broadcast | multicast; Default: ) | Matches source address type:
|
| src-port (integer[-integer]: 0..65535; Default: ) | List of source ports and ranges of source ports. Applicable only if a protocol is TCP or UDP. |
| tcp-flags (ack | cwr | ece | fin | psh | rst | syn | urg; Default: ) | Matches specified TCP flags
|
| src-mac-address (MAC address; Default: ) | Matches the source MAC address of the packet |
| tcp-mss (integer[-integer]: 0..65535; Default: ) | Matches the TCP MSS value of an IP packet |
| time (time-time,sat | fri | thu | wed | tue | mon | sun; Default: ) | Allows to create a filter based on the packets' arrival time and date or, for locally generated packets, departure time and date |
| to-addresses (IP address[-IP address]; Default: 0.0.0.0) | Replace the original address with the specified one. Applicable if action is dst-nat, netmap, same, src-nat |
| to-ports (integer[-integer]: 0..65535; Default: ) | Replace the original port with the specified one. Applicable if action is dst-nat, redirect, masquerade, netmap, same, src-nat |
Stats
| Property | Description |
|---|---|
| bytes (integer) | The total amount of bytes matched by the rule |
| packets (integer) | The total amount of packets matched by the rule |
...