Introduction
The ZeroTier network hypervisor is a self-contained network virtualization engine that implements an Ethernet virtualization layer similar to VXLAN built atop a cryptographically secure global peer-to-peer network. It provides advanced network virtualization and management capabilities on par with an enterprise SDN switch, but across both local and wide area networks and connecting almost any kind of app or device.
MikroTik has added ZeroTier to RouterOS v7.1rc2 as a separate package for the ARM/ARM64 architecture.
Wait, so what can I use it for?
- Hosting a game server at home (useful for LAN only games) or simply creating a LAN party with your friends;
- Accessing LAN devices behind NAT directly;
- Accessing LAN devices via SSH without opening port to the Internet;
- Using your local Pi-Hole setup from anywhere via the Internet;
Required Network Configuration
What ports does ZeroTier use?
It listens on three 3 UDP ports:
- 9993 - The default
- A random, high numbered port derived from your ZeroTier address
- A random, high numbered port for use with UPnP/NAT-PMP mappings
That means your peers could be listening on any port. To talk with them directly, you need to be able to send them to any port.
Recommended Local Network and Internet Gateway Configuration
These ZeroTier recommended guidelines are consistent with the vast majority of typical deployments using commodity gateways and access points:
- Don't restrict outbound UDP traffic.
- Supporting either UPnP or NAT-PMP on your network can greatly improve performance by allowing ZeroTier endpoints to map external ports and avoid NAT traversal entirely.
- IPv6 is recommended and can greatly improve direct connection reliability if supported on both ends of a direct link. If present it should be implemented without NAT (NAT is wholly unnecessary with IPv6 and only adds complexity) and with a stateful firewall that permits bidirectional UDP conversations.
- Don't use "symmetric" NAT. Use "full cone" or "port restricted cone" NAT. Symmetric NAT is extremely hostile to peer-to-peer traffic and will degrade VoIP, video chat, games, WebRTC, and many other protocols as well as ZeroTier.
- No more than one layer of NAT should be present between ZeroTier endpoints and the Internet. Multiple layers of NAT introduce connection instability due to chaotic interactions between states and behaviors at different levels. No Double NAT.
- NATs should have a port mapping or connection timeout no shorter than 60 seconds.
- Place no more than about 16,000 devices behind each NAT-managed external IP address to ensure that each device can map a sufficient number of ports.
- Switches and wireless access points should allow direct local traffic between local devices. Turn off any "local isolation" features. Some switches might allow finer-grained control, and on these, it would be sufficient to allow local UDP traffic to/from 9993 (or in general).
Configuration example
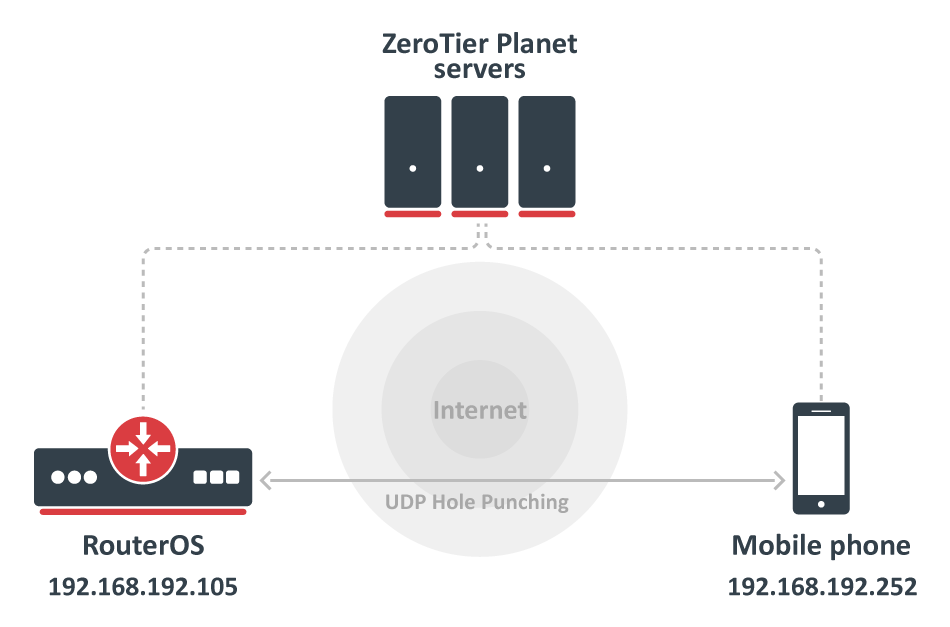
By default, ZeroTier is designed to be zero-configuration. A user can start a new ZeroTier node without having to write configuration files or provide the IP addresses of other nodes. It’s also designed to be fast. Any two devices in the world should be able to locate each other and communicate almost instantly so the following example will enable ZeroTier on RouterOS device and connect one mobile phone using the ZeroTier application.
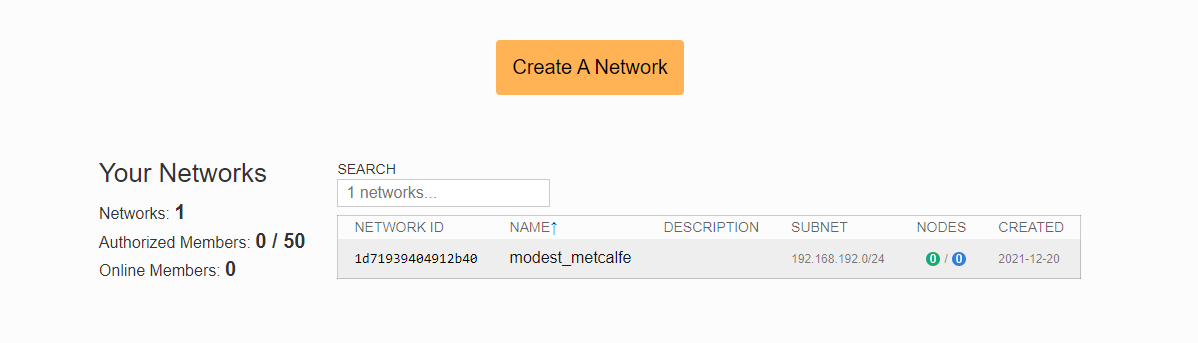
- Register on my.zerotier.com and Create A Network, obtain the Network ID, in this example: 1d71939404912b40;
- Download and Install ZeroTier NPK package in RouterOS, you can find under in the "Extra packages", upload package on the device and reboot the unit;
Enable the default (official) ZeroTier instance:
[admin@mikrotik] > zerotier/enable zt1
Add a new network, specifying the network ID you created in the ZeroTier cloud console:
[admin@mikrotik] zerotier/interface/add network=1d71939404912b40 instance=zt1
Verify ZeroTier configuration:
[admin@MikroTik] > zerotier/interface/print Flags: R - RUNNING Columns: NAME, MAC-ADDRESS, NETWORK, NETWORK-NAME, STATUS # NAME MAC-ADDRESS NETWORK NETWORK-NAME STATUS 0 R zerotier1 42:AC:0D:0F:C6:F6 1d71939404912b40 modest_metcalfe OK
Now you might need to allow connections from the ZeroTier interface to your router, and optionally, to your other LAN interfaces:
[admin@mikrotik] /ip firewall filter> add action=accept chain=forward in-interface=zerotier1 place-before=0 [admin@mikrotik] /ip firewall filter> add action=accept chain=input in-interface=zerotier1 place-before=0
- Install a ZeroTier client on your smartphone or computer, follow the ZeroTier manual on how to connect to the same network from there.
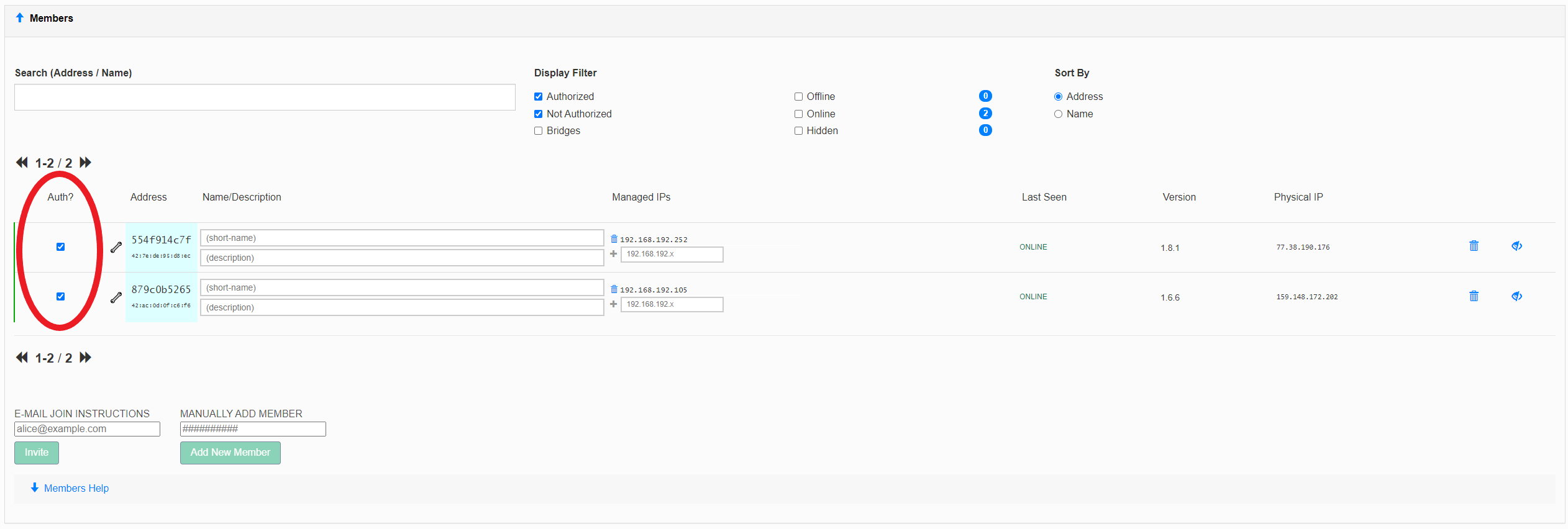
- If "Access Control" is set to "Private", you must authorize nodes before they become members:
[admin@MikroTik] > ip/address/print where interface~"zero" Flags: D - DYNAMIC Columns: ADDRESS, NETWORK, INTERFACE # ADDRESS NETWORK INTERFACE 3 D 192.168.192.105/24 192.168.192.0 zerotier1 [admin@MikroTik] > ping 192.168.192.252 count=3 SEQ HOST SIZE TTL TIME STATUS 0 192.168.192.252 56 64 407us 1 192.168.192.252 56 64 452us 2 192.168.192.252 56 64 451us sent=3 received=3 packet-loss=0% min-rtt=407us avg-rtt=436us max-rtt=452us
You should specify routes to specific internal subnets in the ZeroTier cloud console, to make sure you can access those networks when connecting from other devices.
Peer
zerotier/peer/
ZeroTier`s peer is an informative section with a list of nodes that your node knows about. Nodes can not talk to each other unless they are joined and authorized on the same network.
[admin@Home] > zerotier/peer/print Columns: INSTANCE, ZT-ADDRESS, LATENCY, ROLE, PATH # INSTANCE ZT-ADDRESS LATENCY ROLE PATH 0 zt1 61d294b9cb 186ms PLANET active,preferred,50.7.73.34/9993,recvd:4s526ms 1 zt1 62f865ae71 270ms PLANET active,preferred,50.7.252.138/9993,recvd:4s440ms,sent:9s766ms 2 zt1 778cde7190 132ms PLANET active,preferred,103.195.103.66/9993,recvd:4s579ms,sent:9s766ms 3 zt1 992fcf1db7 34ms PLANET active,preferred,195.181.173.159/9993,recvd:4s675ms,sent:4s712ms 4 zt1 159924d630 130ms LEAF active,preferred,34.121.192.xx/21002,recvd:3s990ms,sent:3s990ms
Parameters
[admin@MikroTik] > zerotier/
| Property | Description |
|---|---|
| name (string; default: zt1) | Instance name. |
| port (number; default: 9993) | Port number the instance listen to. |
| identity (string; default) | Instance 40-bit unique address. |
| interface (string; default: all) | Interfaces ZeroTier uses to. |
| route-distance (number; default: 1 ) | Route distance for routes obtained from planet/moon servers. |
[admin@MikroTik] > zerotier/interface/
| Property | Description |
|---|---|
| allow-default (string; yes | no) | A network can override systems default route (force VPN mode). |
| allow-global (string; yes | no) | ZeroTier IP addresses and routes can overlap public IP space. |
| allow-managed (string; yes | no) | ZeroTier managed IP addresses and routes are assigned. |
| arp-timeout ( number; default: auto) | ARP timeouts value. |
| comment (string; Default: ) | Descriptive comment for the interfaces. |
| copy-from | Allows copying existing interfaces configuration. |
| disable-running-check (string; yes | no) | Force interface in "running" state. |
| instance (string; Default: zt1) | ZeroTier instance name. |
| name (string; default: zerotier1) | A short name. |
| network (string; Default) | 16-digit network ID. |