...
| Note |
|---|
This configuration example is not possible for devices with the Atheros8316 and Atheros7240 switch chips. For devices with QCA8337 and Atheros8327 switch chips it is possible to use any other default-vlan-id as long as it stays the same on switch-cpu and trunk ports. For devices with Atheros8227 switch chip only default-vlan-id=0 can be used and trunk port must use vlan-header=leave-as-is. |
Inter-VLAN routing
Many MikroTik's devices come with a built-in switch chip that can be used to greatly improve overall throughput when configured properly. Devices with a switch chip can be used as a router and a switch at the same time, this gives you the possibility to use a single device instead of multiple devices for your network.
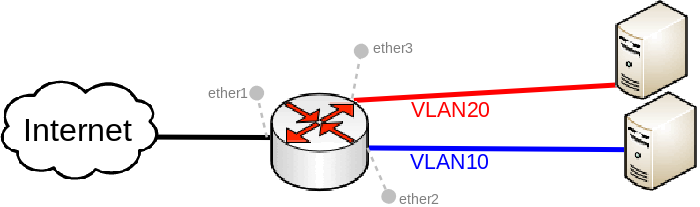 Image Added
Image Added
For this type of setup to work, you must switch all required ports together
| Code Block |
|---|
|
/interface bridge
add name=bridge1
/interface bridge port
add bridge=bridge1 interface=ether2 hw=yes
add bridge=bridge1 interface=ether3 hw=yes |
Create a VLAN interface for each VLAN ID and assign an IP address to it:
| Code Block |
|---|
|
/interface vlan
add interface=bridge1 name=VLAN10 vlan-id=10
add interface=bridge1 name=VLAN20 vlan-id=20
/ip address
add address=192.168.10.1/24 interface=VLAN10
add address=192.168.20.1/24 interface=VLAN20 |
Setup a DHCP Server for each VLAN:
| Code Block |
|---|
|
/ip pool
add name=POOL10 ranges=192.168.10.100-192.168.10.200
add name=POOL20 ranges=192.168.20.100-192.168.20.200
/ip dhcp-server
add address-pool=POOL10 disabled=no interface=VLAN10 name=DHCP10
add address-pool=POOL20 disabled=no interface=VLAN20 name=DHCP20
/ip dhcp-server network
add address=192.168.10.0/24 dns-server=8.8.8.8 gateway=192.168.10.1
add address=192.168.20.0/24 dns-server=8.8.8.8 gateway=192.168.20.1 |
Enable NAT on the device:
| Code Block |
|---|
|
/ip firewall nat
add action=masquerade chain=srcnat out-interface=ether1 |
Add each port to the VLAN table and allow these ports to access the CPU in order to make DHCP and routing work:
| Code Block |
|---|
|
/interface ethernet switch vlan
add independent-learning=yes ports=ether2,switch1-cpu switch=switch1 vlan-id=10
add independent-learning=yes ports=ether3,switch1-cpu switch=switch1 vlan-id=20 |
Specify each port to be as an access port, enable secure VLAN mode on each port and on the switch1-cpu port:
| Code Block |
|---|
|
/interface ethernet switch port
set ether2 default-vlan-id=10 vlan-header=always-strip vlan-mode=secure
set ether3 default-vlan-id=20 vlan-header=always-strip vlan-mode=secure
set switch1-cpu vlan-mode=secure |
| Note |
|---|
On QCA8337 and Atheros8327 switch chips, a default vlan-header=leave-as-is property should be used. The switch chip will determine which ports are access ports by using the default-vlan-id property. The default-vlan-id should only be used on access/hybrid ports to specify which VLAN the untagged ingress traffic is assigned to. |
If your device has a switch rule table, then you can limit access between VLANs on a hardware level. As soon as you add an IP address on the VLAN interface you enable inter-VLAN routing, but this can be limited on a hardware level while preserving DHCP Server and other router-related services. To do so, use these ACL rules. With this type of configuration, you can achieve isolated port groups using VLANs.
| Code Block |
|---|
|
/interface ethernet switch rule
add dst-address=192.168.20.0/24 new-dst-ports="" ports=ether2 switch=switch1
add dst-address=192.168.10.0/24 new-dst-ports="" ports=ether3 switch=switch1 |
See also
