...
| Property | Description |
|---|---|
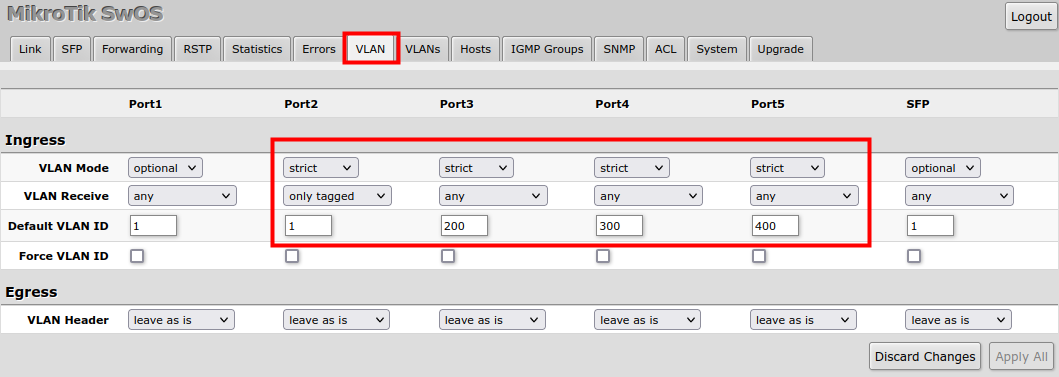
| VLAN Mode | VLAN mode for ingress port:
|
| VLAN Receive | Defines the type of allowed packets on ingress port:
|
| Default VLAN ID | the switch will treat both untagged and "Default VLAN ID" tagged ingress packets as they are tagged with this VLAN ID. It is also used to untag egress traffic if the packet's VLAN ID matches "Default VLAN ID". The VLAN tag itself will only be added if there is VLAN Header = add if missing specified on the egress port |
| Force VLAN ID | Whether to apply Default VLAN ID to incoming packets with VLAN tag |
| VLAN Header |
|
| Warning |
|---|
CSS106 devices running SwOS version 2.12 can filter RSTP BPDU packets when enabling VLAN filtering on ports (VLAN Mode enabled or strict). With SwOS version 2.13, it is recommended to set VLAN Receive to any on trunk ports. |
| Info |
|---|
VLAN modes |
...
| Warning |
|---|
CSS106 devices running SwOS version 2.12 can filter RSTP BPDU packets when enabling VLAN filtering on ports (VLAN Mode enabled or strict). With SwOS version 2.13, it is recommended to set VLAN Receive to "any" on trunk ports. |
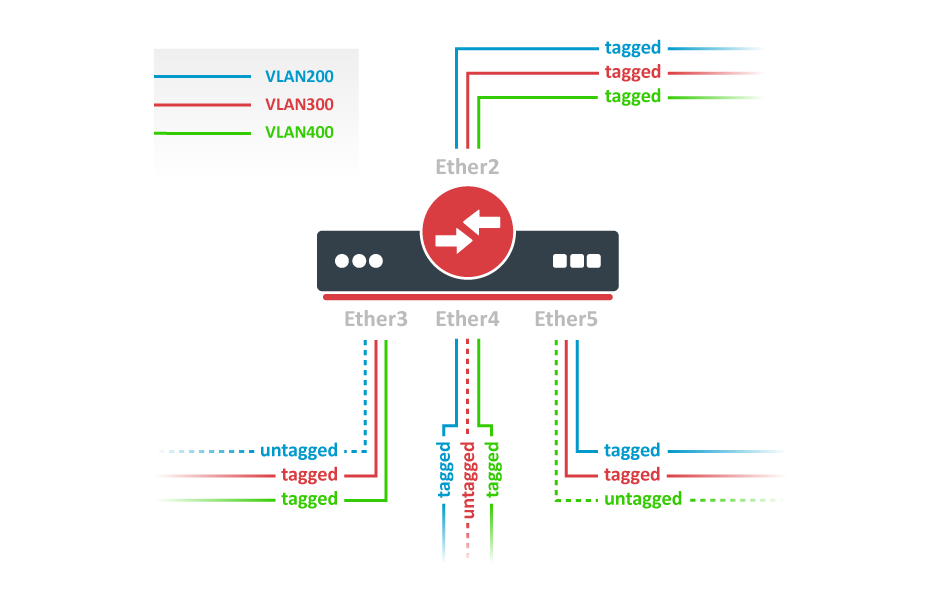
Trunk and Hybrid Ports
...
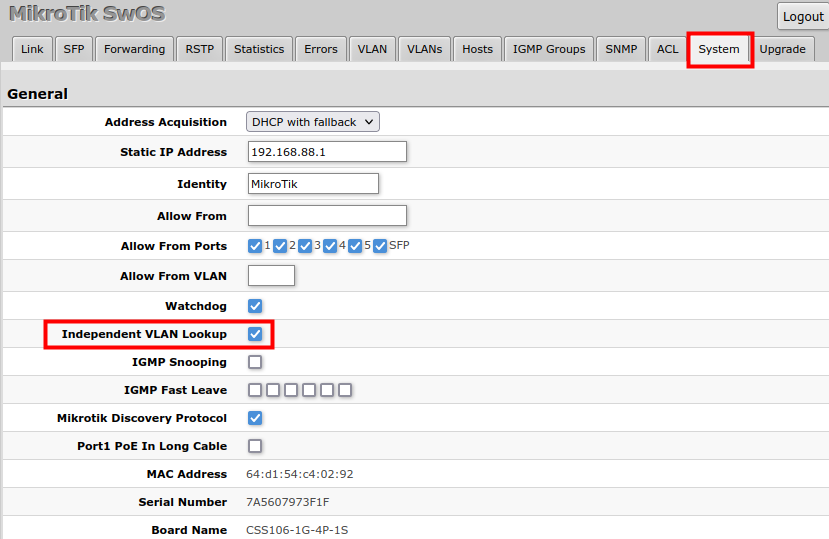
1. In the System menu enable independent VLAN learning (IVL).
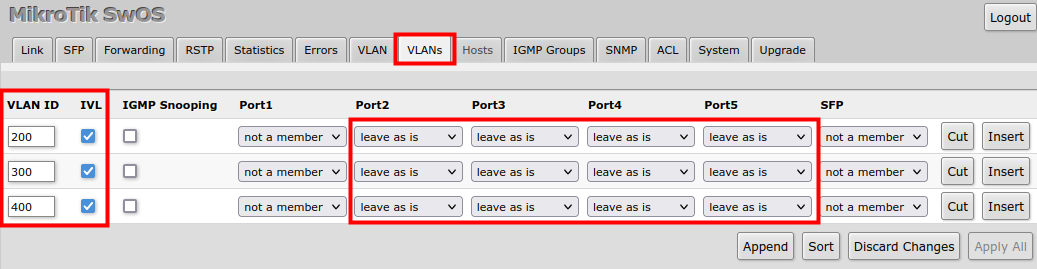
2. In the VLANs menu add VLAN entries, specify port membership, and enable IVL. The default "leave as is" port setting can be used, the tagging and untagging behavior can be changed with the "Default VLAN ID" setting, see the next step.
3. In the VLAN menu configure Default VLAN ID on planned hybrid ports (for untagged VLAN), select the correct VLAN Receive setting (Port2 only tagged, Port3-5 any), and enable strict VLAN filtering to ensure only allowed VLANs can pass through the ports.
| Warning |
|---|
CSS106 devices running SwOS version 2.12 can filter RSTP BPDU packets when enabling VLAN filtering on ports (VLAN Mode enabled or strict). With SwOS version 2.13, it is recommended to set VLAN Receive to any on trunk ports. |
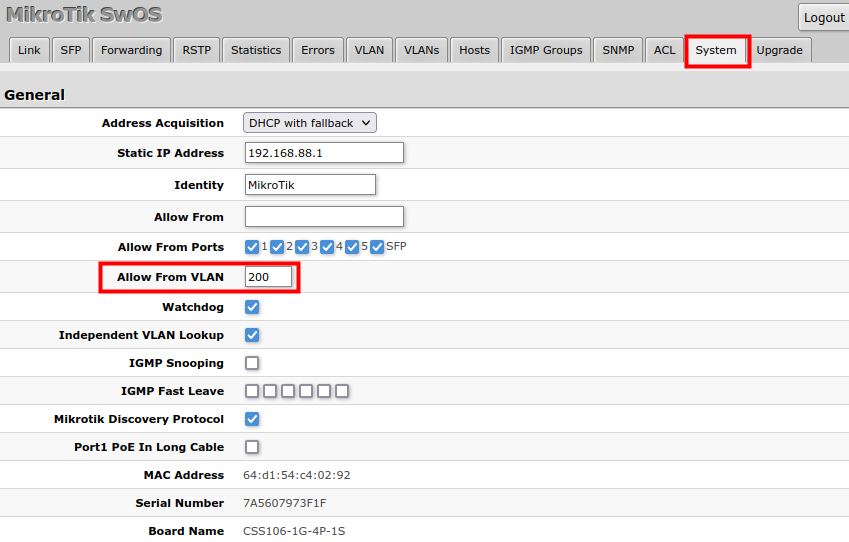
Management access
In this example, switch management access on VLAN 200 will be created. The configuration scheme is the same as "Trunk and Access Ports" and 1., 2., 3. configuration steps are identical. The additional 4th step requires specifying the management VLAN ID in the System menu. After applying the configuration, the switch will only respond to tagged VLAN 200 packets on Port2 and untagged packets on Port3. The DHCP client will also work in the specified VLAN ID.
| Note |
|---|
Changing management VLAN can completely disable access to the switch management if VLAN settings are not correctly configured. Save a configuration backup before changing this setting and use Reset in case management access is lost. |
Hosts
...
This table represents dynamically learned MAC address to port mapping entries. It can contain two kinds of entries: dynamic and static. Dynamic entries get added automatically, this is also called a learning process: when a switch receives a packet from a certain port, it adds the packet's source MAC address X and port it received the packet from to host table, so when a packet comes in with destination MAC address X it knows to which port it should forward the packet. If the destination MAC address is not present in the host table then it forwards the packet to all ports in the group (flood). Dynamic entries take about 5 minutes to time out.
...