Introduction
Internet Protocol Security (IPsec) is a set of protocols defined by the Internet Engineering Task Force (IETF) to secure packet exchange over unprotected IP/IPv6 networks such as the Internet.
...
| Property | Description |
|---|
| accounting (yes | no; Default: ) | Whether to send RADIUS accounting requests to RADIUS server. Applicable if EAP Radius (auth-method=eap-radius) or pre-shared key with XAuth authentication method (auth-method=pre-shared-key-xauth) is used. |
| interim-update (time; Default: ) | Interval between each consecutive RADIUS accounting Interim update. Accounting must be enabled. |
| xauth-use-radius (yes | no; Default: ) | Whether to use Radius client for XAuth users or not. |
Application Guides
RoadWarrior client with NAT
Consider setup as illustrated below. RouterOS acts as a RoadWarrior client connected to Office allowing access to its internal resources.
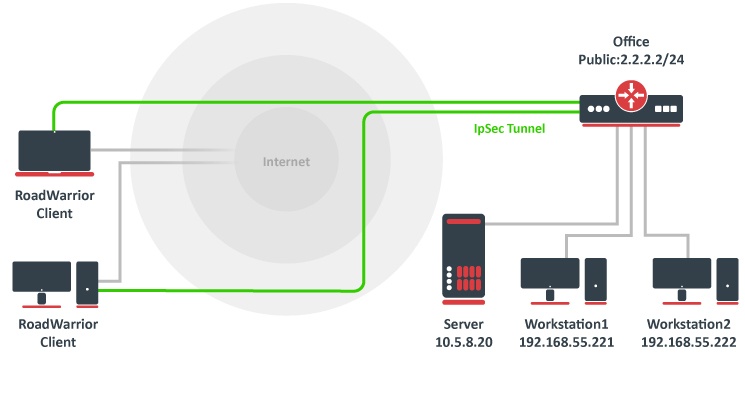 Image Added
Image Added
Tunnel is established, local mode-config IP address is received and a set of dynamic policies are generated.
| Code Block |
|---|
|
[admin@mikrotik] > ip ipsec policy print
Flags: T - template, X - disabled, D - dynamic, I - invalid, A - active, * - default
0 T * group=default src-address=::/0 dst-address=::/0 protocol=all proposal=default template=yes
1 DA src-address=192.168.77.254/32 src-port=any dst-address=10.5.8.0/24 dst-port=any protocol=all
action=encrypt level=unique ipsec-protocols=esp tunnel=yes sa-src-address=10.155.107.8
sa-dst-address=10.155.107.9 proposal=default ph2-count=1
2 DA src-address=192.168.77.254/32 src-port=any dst-address=192.168.55.0/24 dst-port=any protocol=all
action=encrypt level=unique ipsec-protocols=esp tunnel=yes sa-src-address=10.155.107.8
sa-dst-address=10.155.107.9 proposal=default ph2-count=1 |
Currently only packets with source address of 192.168.77.254/32 will match the IPsec policies. For local network to be able to reach remote subnets, it is necessary to change the source address of local hosts to the dynamically assigned mode config IP address. It is possible to generate source NAT rules dynamically. This can be done by creating a new address list which contains of all local networks that NAT rule should be applied. In our case, it is 192.168.88.0/24.
| Code Block |
|---|
|
/ip firewall address-list add address=192.168.88.0/24 list=local-RW |
By specifying the address list under mode-config initiator configuration, a set of source NAT rules will be dynamically generated.
| Code Block |
|---|
|
/ip ipsec mode-config set [ find name="request-only" ] src-address-list=local-RW |
When the IPsec tunnel is established, we can see the dynamically created source NAT rules for each network. Now every host in 192.168.88.0/24 is able to access Office's internal resources.
| Code Block |
|---|
|
[admin@mikrotik] > ip firewall nat print
Flags: X - disabled, I - invalid, D - dynamic
0 D ;;; ipsec mode-config
chain=srcnat action=src-nat to-addresses=192.168.77.254 dst-address=192.168.55.0/24 src-address-list=local-RW
1 D ;;; ipsec mode-config
chain=srcnat action=src-nat to-addresses=192.168.77.254 dst-address=10.5.8.0/24 src-address-list=local-RW |
