...
MikroTik has added ZeroTier to RouterOS v7.1rc2 as a separate package for the ARM/ARM64 architecture.
...
Configuration example
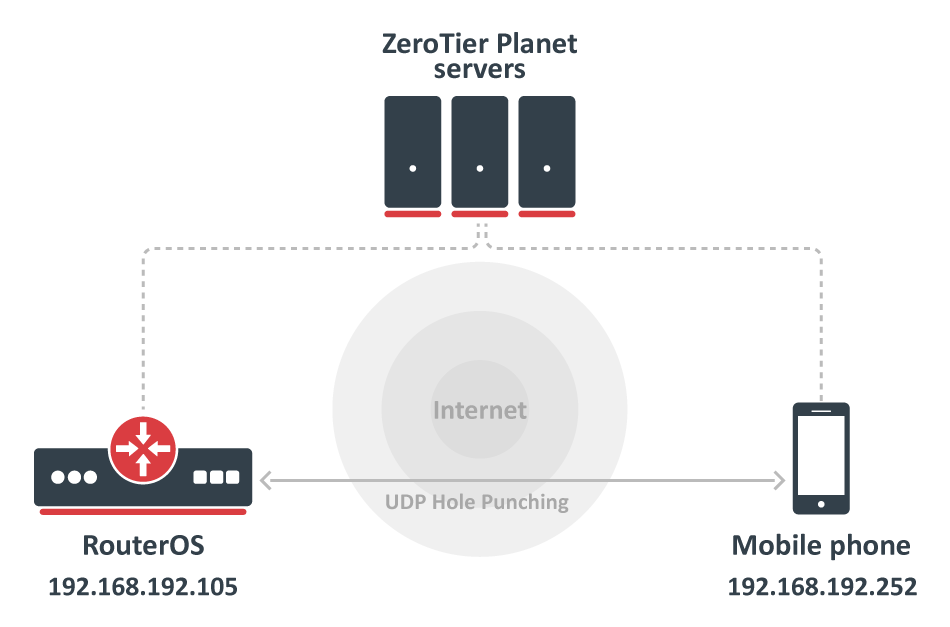
By default, ZeroTier is designed to be zero-configuration. A user can start a new ZeroTier node without having to write configuration files or provide the IP addresses of other nodes. It’s also designed to be fast. Any two devices in the world should be able to locate each other and communicate almost instantly so the following example will enable ZeroTier on RouterOS device and connect one mobile phone using the ZeroTier application.
...
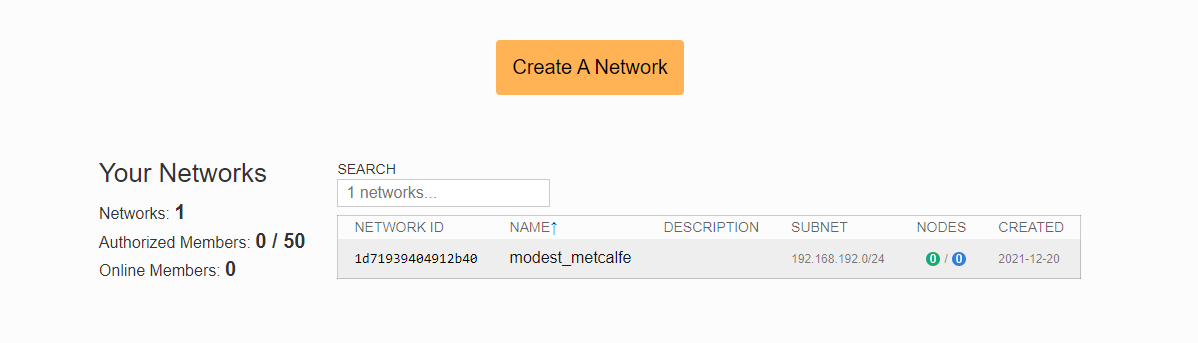
- Register on my.zerotier.com and create your network Create A Network, obtain the Network ID XXXXXXXXX, in this example: 1d71939404912b40;
- Download and Install ZeroTier NPK package in RouterOS, you can find under in the "Extra packages", upload package on the device and reboot the unit;
Enable the default (official) ZeroTier instance:
Code Block language ros [admin@mikrotik] > zerotier/enable zt1
Add a new network, specifying the network ID you created in the ZeroTier cloud console:
Code Block language ros [admin@mikrotik] zerotier/interface/add network=8286ac0e473d****1d71939404912b40 instance=zt1
Note If an "Access Control" is configured in the "Private" state, then you have to allow RouterOS authorization under Networks "members" section.
Now you might need to allow connections from the ZeroTier interface to your router, and optionally, to your other LAN interfaces:
Code Block language ros [admin@mikrotik] /ip firewall filter> add action=accept chain=forward in-interface=zerotier1 place-before=0 [admin@mikrotik] /ip firewall filter> add action=accept chain=input in-interface=zerotier1 place-before=0Verify ZeroTier configuration:
Code Block language ros [admin@MikroTik] > zerotier/interface/print Flags: R - RUNNING Columns: NAME, MAC-ADDRESS, NETWORK, NETWORK-NAME, STATUS # NAME MAC-ADDRESS NETWORK NETWORK-NAME STATUS 0 R zerotier1 2A42:DDAC:A10D:4C0F:5CC6:C9F6 8286ac0e473d**** testme_mt OK 1d71939404912b40 modest_metcalfe OK
Now you might need to allow connections from the ZeroTier interface to your router, and optionally, to your other LAN interfaces:
Code Block language ros [admin@mikrotik] /ip firewall filter> add action=accept chain=forward in-interface=zerotier1 place-before=0 [admin@mikrotik] /ip firewall filter> add action=accept chain=input in-interface=zerotier1 place-before=0- Install a ZeroTier client on your smartphone or computer, follow the ZeroTier manual on how to connect to the same network from there.
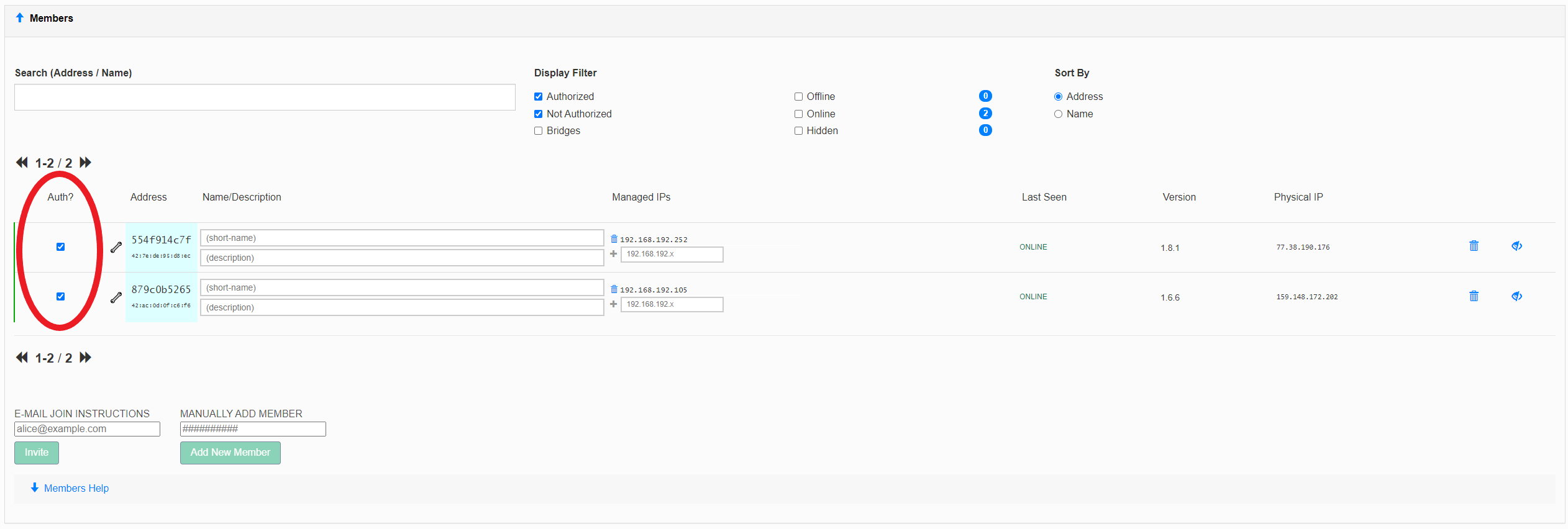
- If "Access Control" is set to "Private", you must authorize nodes before they become members:
| Tip |
|---|
You should specify routes to specific internal subnets in the ZeroTier cloud console, to make sure you can access those networks when connecting from other devices. |
...